IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Integrated Computer Services Blog - Page 2 / 2
Discover the transformative power of 24×7 IT support in safeguarding your business with Integrated Computer Services. In this insightful blog post, we unravel the dynamic landscape of technology challenges and the pivotal role proactive IT support plays. Learn the critical distinction between reactive and proactive approaches, understanding how the latter minimizes downtime, enhances security, and boosts productivity. Integrated Computer Services excels in providing comprehensive 24×7 support services, featuring immediate remote assistance, on-site support, secure desktop connections, and continuous system monitoring. Uncover the advantages of a proactive IT support model, including cost-efficiency and increased productivity. Based in New Jersey, Integrated Computer Services emerges as a trusted partner, offering desktop support, networking, security, and data backup services. Invest in prevention with 24×7 IT support, fortify your IT infrastructure, and propel your business towards sustained growth. Choose Integrated Computer Services – your proactive ally in navigating the complexities of modern technology.
Unlock the potential of your infrastructure with insights into performance and the transformative impact of cloud technology. Explore 8 ways the cloud boosts efficiency, from accelerated scalability and enhanced flexibility to resilience, cost optimization, and innovation empowerment. Discover how security reinforcement, environmental sustainability, and evolving trends shape the future of infrastructure. Contact Integrated Computer Services (ICS) for expert guidance on harnessing the power of the cloud to optimize your operations and reshape the landscape of modern technology.
Explore the pros and cons of Microsoft Cloud Technologies in the evolving workplace. With tools like Microsoft 365, businesses can enhance productivity, support hybrid office models, and benefit from cloud-based advantages. Challenges include a subscription-based model and a learning curve for advanced tools, mitigated by expert assistance for optimal utilization. Unlock the full potential of Microsoft 365 with Integrated Computer Services for a revolutionary modern workplace.
Learn to protect sensitive information when using AI tools like Chat-GPT. Acknowledge the risks associated with these powerful tools, emphasizing they aren't personal confidants. In case of a breach, where sensitive data might be exposed, exercise caution—avoid sharing confidential business information or personally identifiable data. The message underscores the threat to privacy and security from unauthorized access. Users are advised against inputting such information into Chat GPT and encouraged to monitor accounts for suspicious activities. Prioritize information security while leveraging technology for efficiency.
Why settle for traditional when the future of IT leadership is knocking at your door with virtual CIO services? In the ever-evolving business landscape, keeping up with the latest IT developments is a necessity for growing your business. Yet, the luxury of a full-time, in-house Chief Information Officer remains a distant dream for many small and medium-sized businesses. This is where virtual CIO services step in. It's a game-changer that's reshaping how businesses approach technology strategy. This innovative service model provides the expertise and guidance to navigate the complexities of business technology, leveling the playing field for businesses striving for growth and efficiency. As you embark on the path of improving your business, the insights and strategic foresight of a virtual CIO can be your compass. Read on to explore how these services can transform your IT leadership and propel your business forward.
In the face of rising cyber threats, safeguarding sensitive data is paramount for businesses. Two-Factor Authentication (2FA) emerges as a crucial strategy, adding an extra layer of verification during logins or transactions. Unlike traditional methods relying solely on passwords, 2FA demands two distinct forms of identification, significantly bolstering security. Implementation examples include mobile authentication, security tokens, and devices like Google's Titan Security Key. The need for 2FA is underscored by alarming statistics on security breaches and the pervasive threat of identity theft. It acts as a formidable barrier against phishing attacks, secures data and finances, and is swiftly implementable through major accounts. Professional IT support is recommended for seamless integration. In essence, 2FA is not just a security measure but a strategic imperative, fortifying organizations against evolving cyber threats and providing robust defense for valuable data and assets.
In an era dominated by digital transformation, understanding the importance of cloud security is critical. This post delves into the significance of safeguarding digital assets and addresses the shared responsibility in cloud security. It explores potential threats and, rather than just listing them, provides actionable strategies to fortify cloud security. From Multi-Factor Authentication to off-boarding processes, the post offers practical insights to protect against evolving cyber threats. With a focus on user responsibility and the consequences of security breaches, this discussion equips readers with the knowledge needed to navigate the complexities of cloud security and stay secure in the ever-changing digital landscape.
In the fast-paced world of modern business, the integration of Information Technology (IT) is essential for success. Strategic IT consulting, exemplified by IT Consulting Innovators, plays a crucial role in navigating this landscape, offering specialized insights and aligning IT strategies with business objectives. This proactive approach ensures businesses stay ahead of technological trends, mitigate risks, and achieve sustained growth. Key recommendations include IT infrastructure assessment, data security, scalability planning, digital transformation, and optimizing IT costs. Integrated Computer Services champions these strategies for unparalleled IT excellence, operational efficiency, and a distinctive competitive advantage in today's business environment. Connect with them for transformative success.
In response to the increasing threat of ransomware in remote work settings, a comprehensive approach can fortify an organizations' digital assets. This involves implementing robust password policies, integrating two step authentication, and keeping software regularly updated for enhanced cybersecurity. Ongoing employee training, particularly in recognizing and thwarting phishing attempts, plays a critical role in preventing human errors that often lead to ransomware incidents. Stressing the importance of routine data backups, preferably with the assistance of Managed Service Providers, adds an additional layer of protection. Lastly, creating and testing an incident response plan is pivotal for building cybersecurity resilience. For personalized assistance, interested parties are encouraged to reach out to Integrated Computer Services.
In an era where cyber threats loom large, safeguarding vital sectors like law firms, transportation, and healthcare is paramount. Explore the essential role of strategic defense, emphasizing how measures like vulnerability assessments, incident response planning, network segmentation, employee training, and 24x7x365 remote IT support services are vital for fortifying critical infrastructure security. Integrated Computer Services stands at the forefront, offering expertise that goes beyond traditional IT support. Discover how these comprehensive strategies empower industries, ensuring the stability and security of critical infrastructure in an interconnected world. If you're navigating the complex landscape of safeguarding essential systems, this exploration is your guide to resilience and success.
IT support for law firms plays a crucial role in the legal field. The ultimate goal of any law firm is to protect and serve clients, and without proper IT management services and support, achieving this goal is impossible. While you might understand the importance of your IT infrastructure in keeping your business data and files safe, there are several ways that IT support can transform your legal practice’s efficiency you might not consider. So how do IT support services like Integrated Computer Services provide ample resources for law offices to operate safely and optimally, and how can this service transform your practice’s efficiency? Read more to learn how Integrated Computer Services empowers law firms to thrive and succeed.
When deciding between remote and onsite IT support, understanding the pros and cons is crucial. Equally important are key factors that influence your decision, such as infrastructure needs and custom development requirements. Explore the nuances of each approach to make an informed choice tailored to your organization's unique demands. Whether it's the convenience of remote support or the hands-on advantage of onsite assistance, a careful consideration of these factors ensures an optimal IT strategy for your business.
Discover the best IT solutions tailored for the challenges faced by growing small and medium-sized businesses. From Infrastructure-as-a-Service (IaaS) and Private Cloud Solutions to Desktop-as-a-Service (DaaS) and Remote WebApps, each solution addresses specific needs, offering flexibility, scalability, and cost-effectiveness. ICS Secure Cloud seamlessly integrates these solutions, providing cutting-edge technology, enhanced security, and unmatched flexibility to empower businesses on their growth journey.
Navigating the world of IT is a daunting task for many businesses, especially without the help of managed services to make the IT process easier. With the global managed services industry exploding more and more every day, taking advantage of this innovative solution can transform your IT processes. But what are these services, what processes do they entail, and what are the benefits of outsourcing managed services? Read on to find all this and more to help you discover your business's top-managed services solution.
Strategically assessing your IT setup is crucial to optimizing business performance and mastering all tech-related processes in your organization. Unleashing the full potential of your company’s technology infrastructure is possible through a comprehensive IT assessment, like our free IT risk assessment, to secure your IT infrastructure and guarantee that you’re following the best, safest practices for all things IT. With 50 percent of small to medium-sized businesses being the victims of cyber attacks–and with 60 percent of these companies going out of business following the attack–there’s no denying the need for a comprehensive assessment. But how does an IT assessment evaluate your infrastructure for potential threats, and what are the advantages of this assessment? Read more to find everything you need to know about a thorough IT assessment to take your organization’s IT security to the next level.
Cloud migration, simply put, is the process of transferring your business or operation’s digital infrastructure from your platform into the cloud. This can be either a partial or complete transfer to the cloud, but in either case is done to help support your overall operations and protect important company data. Cloud migration offers numerous benefits, both boosting your business security and saving you money that would otherwise go towards maintaining your data center. Cloud scalability is an essential part of this process, supporting your operations as they grow and shift during this migration.
IT infrastructure is a crucial part of day-to-day company operations, even for small businesses! However, for many business owners, setting up digital technology and the related components can be overwhelming. This is especially true if you’re new to the business world or maybe don’t have a background in digital tech. As a small business owner, you don’t have time to learn the world of IT and need to be focused on growing your company. This is where the role of small business IT consulting comes in. This specialized consulting provides specialized technology-related guidance and support to owners looking to streamline their digital operations. Consultants in this field assist with various aspects of information technology, helping maximize efficiency and operations.
Business networks are relatively complex, and even a bare-bones setup can be too complicated to manage for individuals who don’t have significant IT or network management experience. While learning about how your company’s network operates is overall a positive step, it’s far from the most secure option for keeping your system operating with safety and efficiency in mind. Today’s technological landscape introduces so many potential risks to a company’s network. As such, managing your entire networking infrastructure in-house isn’t going to be enough. Without well-rounded network management, the possibility of a system-wide disaster occurring is only a matter of time. Fortunately, expert-managed network services provide businesses with an array of unique solutions they can adopt to keep systems running as intended. Outsourcing these services not only helps companies cut IT costs, but the fully customizable options that providers offer ensure that each business has a system in place that meets its needs.
Windows Server 2012, the operating system some of you are currently utilizing, is approaching its end of life (EOL) date, which is set for October 10, 2023.
Managing your business's IT infrastructure can be challenging, but without proper management of these resources, you cannot provide the amazing service your customers expect from you. As cloud technology becomes increasingly common, more and more businesses are opting for cloud computing support solutions that allow them to utilize this type of technology to help them in this area. As you may already know, there are seemingly endless benefits of cloud computing, from cost savings to enhanced security to improved flexibility. But, while these benefits may be incredibly tempting, you may feel intimidated by the huge variety of options and services available. This article will explore how you can easily determine which support options are the best for your business based on your particular needs and desires.
As cyber threats continue to escalate in both frequency and sophistication, safeguarding your company's sensitive data and maintaining a seamless operation of your IT infrastructure have become critical for success. Now, more than ever, it is essential to prioritize and implement robust security measures to keep your business well-protected. In this article, we’ll discuss six essential steps you can take to check your network security and safeguard your business.
Protecting your business against cyber threats is more important than ever before. With the worldwide cybercrime environment expected to cost 23.82 trillion USD by 2027, businesses without a comprehensive IT security system are leaving themselves–and their data–vulnerable. To combat issues with your company’s cyber security systems, you need to perform a thorough IT security checkup. This process is one of the most effective ways to identify system vulnerabilities and determine solutions to keep your data safe 24/7. But what is the proper process to conduct a thorough IT security checkup? This article will detail the IT security checkup process to ensure that you don’t miss any crucial steps when protecting your organization. Let’s dive in!
In theory, all of the software, platforms, and interfaces you use to run your business would work exactly how you need them to any time you need them. But unfortunately, we do not live in this idealized world, and sometimes even the best technologies can run into issues. So when something goes wrong (and it will, as Murphy’s Law states), your small business needs to have the right measures in place to overcome the problem. Now, you may be able to handle some of the more common IT practices, such as issuing privacy statements and managing your basic IT infrastructure essentials. But, regarding the more complicated aspects of your IT support strategy, you may need to look for external solutions. This is where small business IT services come into the picture. This article will explore why these services are crucial for your business as well as what to look for in an SMB IT support company to ensure you are getting the right solutions for your business’s needs.
The world of information technology is constantly evolving, and keeping up with new technologies and software solutions can be both incredibly time-consuming and expensive. Many businesses utilize outsourced IT services to avoid spending as much time and resources on this incredibly important field while maintaining the benefits of staying up-to-date.
Have unwanted pop-ups or banner ads on your computers ever disrupted your business? If so, you may have fallen victim to common adware. Adware is software that displays advertisements on your device without your permission. While seemingly harmless, the adware can pose serious risks to your business. In this article, we'll explore five common types of adware, the impacts of adware on your business, and, most importantly, how to protect your business from adware.
Your days are tied up with managing your business's office equipment and keeping them running like a dream. But what happens when a network security nightmare shows up at your doorstep?
Are you looking to improve the performance of your business's IT systems? Regular IT maintenance is crucial for the success of any business, yet it's often overlooked.In this article, we'll discuss the importance of IT maintenance, the risks of neglecting it and how regular maintenance can improve your business's performance and network security.
When was the last time you updated your organization's information technology network? Research shows that 75% of companies depend on legacy network technologies, particularly security technologies. Fortunately, a network upgrade can help with improving network performance and reliability, making your network run like a well-oiled machine. It can also enhance your computer network security.
With the right technology infrastructure, your business can thrive. One critical aspect of this infrastructure is the small business server. This article outlines the key factors to consider when choosing a small business server and the benefits of working with an expert server installation company.
Learn how to choose computer support services that fit your team's needs. There are options for small businesses to get computer support within their budget.
When it comes to your business's IT infrastructure, there are several options available to you. You can manage everything in-house, or you can outsource it to a managed service provider. You can also choose to use cloud services or a combination of these options. In this guide, we will explain the different types of IT infrastructure services and help you decide which is best for your business.
Did you know that nearly 20% of businesses fail within the first two years? The good news, however, is that you can take steps to prevent this from happening. Managing your IT systems is one of the most important steps you can take when it comes to the longevity of your company. The best way to do so is by creating an IT system audit checklist. Let's take a look at how you can do so and how it can benefit your IT management.
Did you know that the average SMB spends anywhere from $10-50,000 on IT services per year? Businesses in every industry are always looking for ways to reduce costs and increase profits. When it comes to IT expenses, there are a number of strategies that can be implemented in order to achieve these goals. In this guide, we will take a look at five different IT cost reduction strategies that SMBs can use to save money and improve their bottom line. Implementing even one or two of these strategies can have a significant impact on your company's bottom line!
If you're going to reach new customers, you need to take the tech side of your business very seriously. By 2025, there will be over 70 billion devices connected to the internet in the world. Many of those devices will come from small businesses like the one you operate. The more technology takes over each industry, the more need there is for managed service providers. Hiring a service provider is a no-brainer for anyone running a small business. In this post, we're going to look at some of the managed service provider benefits that you'll see when you hire one. Outsourcing your IT is a big decision, but keep reading, and you'll have 6 clear-cut reasons to find an MSP this year.
Did you know that cybersecurity is one of the most important issues businesses face today? In fact, a study found that 67% of businesses reported a repeat cybersecurity incident in the past twelve months. That's why it's so important for business owners to be aware of the five most critical cybersecurity gaps. In this blog post, we will discuss each gap and provide tips on how to close them. Are you ready? Let's get started!
Did you know the number of internet-capable devices is expected to reach 30 billion in 2022? With so many advances happening, it can feel daunting to keep up. You're either one step ahead or too far behind, and things can quickly become confusing — especially for your business. With changing regulations and new software coming every day, your IT department might have a hard time keeping up. That's where managed IT services can help. Read on to learn 10 of the best types of managed IT services out there.
The latest findings show that small businesses in America are not ready for a cyberattack! An information security plan is a vital part of any company's cyber security strategy. While there are different approaches to a cyber security plan, all of them have the same goal in mind. The goal is always to protect your business from Intruders who want to access your data. Here's a closer look at how to create a comprehensive IT system security plan.
In 2021, cybercrime resulted in over $7 billion lost in the United States alone. That marked a staggering 64% leap from 2020's cybercrime losses. As cybercriminals get bolder, cybersecurity must get more sophisticated. Large corporations often hire a full-time Chief Information Security Officer (CISO). This is an executive tasked with organizing, maintaining, and protecting data. CISOs work at an enterprise-level scale. Most smaller companies can't afford the salary and benefits you need to hire a full-time CISO. Yet, their current teams aren't equipped to manage and protect data effectively. CISO consulting bridges that gap. Virtual CISO consulting services empower small organizations. They manage and protect data with the same strategies big corporations use. Yet, these services only cost a fraction of what corporates pay CISO executives.
Did you know that approximately 47 percent of American adults have had their personal information exposed at the hands of cybercriminals? Information security and network security are terms that are often used interchangeably. Instead, you should consider 'information security' as a canopy term. This term includes other security topics like cryptography as well as cyber security. Nevertheless, it can be challenging to distinguish between the two terms. To learn more about information security vs. network security, continue reading this article!
The entire managed services industry will almost double within just a few years. That is just one indicator of how huge the benefits of managed IT services for small businesses can be. But what are these benefits? Why are more and more businesses turning to managed services to help them with technical needs? Read on to learn all about the most important things to understand about managed IT services and what they can do for you!
More than 45% of all businesses in the United States have experienced at least one data breach at some point in the past. If you're worried about the security of your company's data and information, then you'll need to have a great managed security service provider on your side. But what about MSSP pricing, you might ask? The MSSP costs will vary according to a variety of factors, and you will also need to consider your own budget when deciding on different security options. Keep reading and learn more about MSSP costs and what you can do to find the best options for you and your business.
There is a reason that 66% of small businesses with over 50 employees choose to outsource their IT needs. And the main reason is efficiency. But, what does this mean for your company? If you are wondering if you should start outsourcing IT security then efficiency is a vague term that needs elaboration. Get started with knowing the benefits of outsourcing security services with this top 10 list.
Understanding the differences between managed services vs professional services can help you appreciate why they have so much appeal as well as help you figure out which one is the right choice for you. Read on to learn all about the most important things to understand about managed services, professional services, and what they might be able to do for you!
Just 25 years ago, most organizations were only electronically connected to their internal servers and databases. However, some organizations such as hospitals and universities were "electronically sweet-talked" into the cloud. Small organizations with little IT budget ended up as early cloud adopters. In 2020, 61% of businesses migrated their workloads to the cloud. By doing so, these businesses could plan out and raise their budget for the future. The businesses decided to cut costs and work more efficiently that way. Is that something you feel you could benefit from it? If so, read on to learn more about cloud computing and your options.
New technology is rapidly changing the financial services industry. Is your organization keeping up? Finance IT consulting in NJ can help you stay competitive. You can benefit from a range of support and consulting services. Find out more about the best IT for finance companies and how better IT support can help your business.
IT support for startups can be easily put to the wayside, but that attitude can lead to trouble when you need tech support. In fact, there are a lot of benefits that come with startups having dedicated IT support. Read on to learn more.
Setting up the IT infrastructure for your small business can be a daunting task. There are many components to consider, and it can be hard to know where to start. That's why we've created this small business IT infrastructure checklist. This guide will walk you through the steps you need to set up a solid foundation for your business's technology needs. Follow these steps, and you'll be well on your way to having a thriving small business:
There are many businesses in Jersey City, and each of these businesses need a solid IT support service to keep their business running smoothly and efficiently. Thankfully, at Integrated Computer Services, we can do just that. Are you looking for IT support in Jersey City? Keep reading to learn more!
Understanding the differences between managed services vs. outsourcing can help you appreciate why people often choose one of these options to help them with their technical needs. It can also help you decide which one is the right choice for you. Read on to learn about the critical differences between managed services and outsourcing options.
Emergency IT support services do not need to happen in-house. Outsourcing your IT support offers many benefits to your company, clients, and employees. Understanding the benefits of outsourcing these vital services and how Integrated Computer Services meets these needs, ensures that your business is always up and running.
Despite these risks, the cloud is more popular than ever. What’s more, for certain things, like data storage, managed services and IT security, using a cloud service can definitely be much more practical, robust, secure and not to mention affordable than hosting your own version of these or other services. This is why cloud migration is huge, useful and often necessary. The question then is why and, briefly, how it works. Here’s a breakdown of the main reasons and techniques for sending data over to distant servers.
In sprawling New Jersey, it's vital that your business has the best IT solutions. With technology dominating every aspect of business, you need to make sure your processes are secure and protected and you're leveraging the elevation expert software consultancies can offer. This comprehensive article will walk you through the top IT companies in New Jersey.
In sprawling New Jersey, it's vital that your business has the best IT solutions. With technology dominating every aspect of business, you need to make sure your processes are secure and protected and you're leveraging the elevation expert software consultancies can offer. This comprehensive article will walk you through the top IT companies in New Jersey.
How do companies choose the best IT firms when there are so many in business today? Here, we’ll explore what to look for in an IT company, helping you select the ideal IT support provider for your unique needs.
Engineers have a unique set of needs when it comes to information technology. Often, in-house IT staff are not enough to meet the demands of a growing engineering company. It is where managed IT services come into the picture. This post will discuss what engineers need to look for when choosing a Managed Service Provider (MSP) and how managed IT services for engineers can help your business grow.
If you're like most business owners, you probably wear a lot of hats. You're responsible for marketing your business, making sales, and providing customer service. But what about technology? Do you have the time or expertise to manage your company's IT needs? If not, it may be time for IT consulting in Parsippany, NJ. This blog post will discuss the six benefits of doing so! Keep reading to learn more.
Newness, especially with a price tag attached, is daunting. But we live in a tech-centric world, and making timeous decisions can position businesses well for growth and profitability. The financial benefits of cloud computing, for example, vastly outweigh the costs of migrating. Below, we look at some of the economic advantages of moving to the cloud.
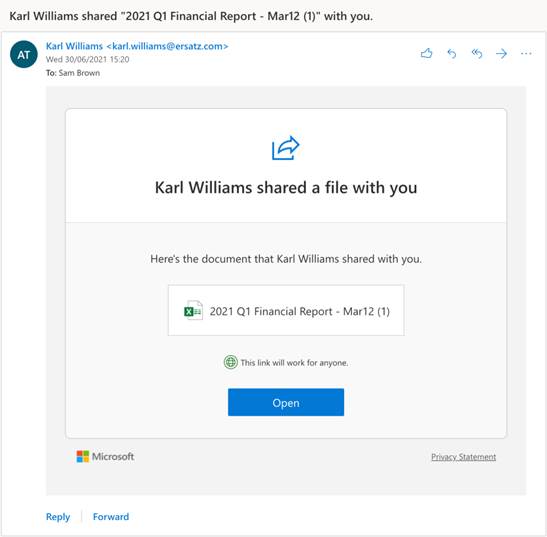
With the Russian invasion of Ukraine dominating news headlines, malicious actors are using the issue as an email phishing hook, targeting Microsoft users with warnings of “unusual sign-on activity” from Russia.
As a small or medium-sized business, you probably spend a lot of time concerned with IT. Those concerns might even be headaches at times. Hiring IT staff, IT salaries, software and hardware upgrades, IT can take a toll on your time and budget. This is why many companies are focusing on what they do best–their products or services–and outsourcing their IT needs to companies who can provide them with the solutions they need.
Keeping track of multiple passwords is not easy, but it’s essential. Unfortunately, too many people are letting emotions drive dangerous password habits. 68% of people who reuse passwords do so because they’re afraid of forgetting them, even though 79% of respondents agree that compromised passwords are troubling. Control is an important factor: 52% who reuse passwords want to control all their passwords and feel that using the same password everywhere is the only way to accomplish that. Of course, that makes it easier for hackers too.
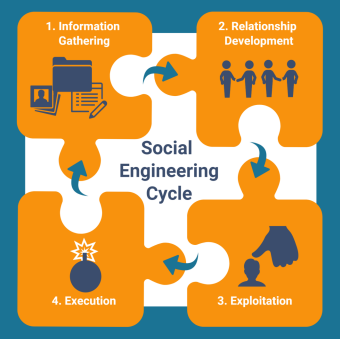
All organizations think it won’t happen to them, but phishing isn’t a trap that only ensnares the gullible or those unacquainted with technology. Far from it. Gone are the days of poorly-worded, patently obvious attempts at scamming users out of their hard-earned cash. Some of today’s most sophisticated phishing attacks are almost indistinguishable from legitimate business communications – they’re well-written, thoroughly researched, and establish a thread of communication with the victim before attempting to steal their credentials, bank balance, or ask them to send gift cards.
In today’s digital age, cybercrime is on the rise, and the number of breaches experienced by businesses and individuals is only growing. This year, we’ve exceeded the number of breaches seen in 2020. As businesses and organizations become more reliant on technology, they become more vulnerable to cyberattacks. Hackers are finding new and innovative ways to gain access to data, and it’s more important than ever for businesses to have robust cybersecurity measures in place.
Business email compromise (BEC)—also known as email account compromise (EAC)—is one of the most financially damaging online crimes. It exploits the fact that so many of us rely on email to conduct business—both personal and professional.In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request.
Unfortunately, No business, organization, or individual is immune to cybercrime. Every employee of an organization, from the CEO on down, is responsible for understanding basic cyber hygiene steps to protect themselves.
One of the biggest, lethal, and common web security threats facing small businesses is phishing. A phishing scam is where the threat actor, pretending to be a legitimate and reputable institution/individual, drafts and sends email/SMS or other communication to obtain sensitive information, gain access to networks, infect systems with malware, and so on.
The massive exploit of SolarWinds last year is a prime example of what is called a “supply chain” vulnerability. The vast majority of those impacted by the Russian SolarWinds attack probably had never even heard of the company SolarWinds and did not realize that they were dependent upon that company for critical infrastructure. Indeed, modern supply chains, manufacturing, technology, and Internet and telecommunications networks are dependent upon complex webs of supply chains—or, more accurately, supply webs—which are vulnerable to disruption and attack.
If you run a business, you need to do everything you can to make sure your business remains operational. That is why a Business Continuity Plan is important.
What is a Business Continuity Plan, and why does your small business need one? Make sure you rely on experienced IT professionals who can help you ensure your business can stay up and running in the event something happens to your network.
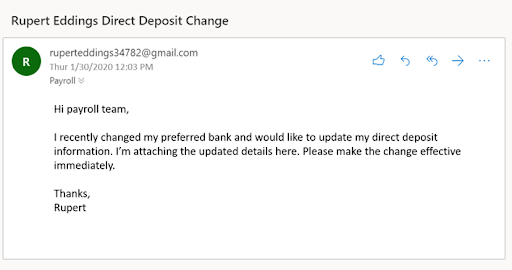
More InfoRecently, there has been an increase in the number of employers across the country who have been targeted by payroll fraudsters. Scammers continue to get more resourceful, cunning, and technically savvy in their attempts to defraud victims by gaining access to financial accounts as well as valuable personal information.
In today’s rapidly changing environment, SMBs need access to the same types of technologies large companies do. Unfortunately, they typically don’t have the budget to support this need.
Many small businesses don’t have a robust IT team able to manage all of their technology needs. Aside from staffing, it’s costly to maintain full-time employees dedicated to each area of technology, especially as the risks associated with cyber threats continue to grow. As a solution, SMBs frequently turn to managed IT service providers (MSPs) to fulfill their technology needs.
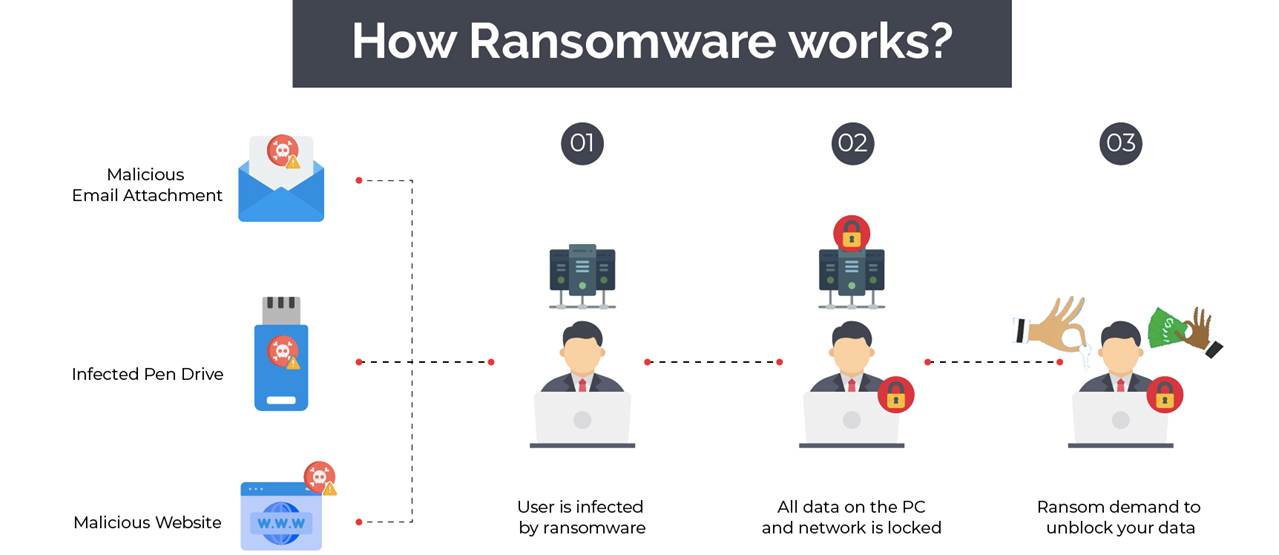
Ransomware is one of the biggest cybersecurity threats to businesses today, and cybercriminals can potentially make millions of dollars in a single successful attack. Now, cybersecurity researchers have discovered a ransomware campaign asking employees to install ransomware on their organization’s network, in return for a slice of the payout.
Threat actors and malicious hackers have continually been creating malware in several ‘unique’ programming languages to help circumvent & evade security protections and analysis, which can severely impact the ability to reverse engineer the malware.
Throughout 2020 and 2021 we’ve seen a spike in cyberattacks, spam, hacks, and attempted hacks nationwide and globally. The spike in overall cyberattacks has prompted world leaders to step up their defenses, as well as to increase the public’s understanding of these attacks, and how to defend themselves from common threats.
Most people are familiar with ransomware. We’ve read news stories detailing the computer plague that has been targeting industries for the past few decades as well as the high-profile ransomware attacks against large organizations in these last few months.
Please be aware of the following phishing techniques designed to get full control of your email mailbox.
IT departments within small & medium-sized businesses (SMB) can become targets for threats, where they may be attacked and compromised due to a single source, or cyber-attack. In most cases, these SMB IT departments are responsible for the businesses IT environment, which can be an overwhelming task if the SMBs are constant targets. Managed IT Services can assist organizations to manage, monitor, and maintain their networks to streamline processes for SMB organizations.
Due in large part to COVID-19 and the increased prevalence of remote work, ransomware attacks dominated 2020, and experts predict there will be at least twice as many cases of data theft in the 2021.
It’s been a boom time for social engineering. Pandemic panic, desperation as income concerns grew, and worry over health and wellness made it easier for criminals to tap into fear.
Most enterprise applications would be located securely in data centers, where company employees would connect to internal networks with data being accessed by a network perimeter, keeping assets safe. With Cloud network security technology and the pandemic affecting in-office work, the Cloud is being leverages more than ever.
As the workplace has changed throughout 2020-2021 employees and employers have been given a challenge of adapting to a remote workforce. One of the most important challenges for any business with a remote workforce is to ensure that your networks security defenses are top-notch.
Each week, organizations are breached by hackers who have one goal: extort money.In May 2021, at least 160 organizations in the United States informed their customers and partners that they had been breached. While data breaches are typically thought of as opportunities to steal and resell data, many incidents have fraud or some other direct monetization method as their primary motive. Ransomware and business email compromise attacks are the best examples of these types of events, but many identity fraud schemes are much easier to commit when bad actors gain direct access to a business’s systems.
Managed IT services is a third-party service that encompasses all IT functions and responsibilities. You managed IT service provider is responsible for your small business’ IT infrastructure up-time and security. Businesses usually outsource their IT management and support due to the plentiful resources needed for a robust IT infrastructure.
As a small to medium business owner, you may have thought about the pros and cons of having internal or outsourced IT services. There are benefits to both, but the right decision usually comes down to the specific needs of the individual organization.
Outsourcing enables organizations to expand or replace their internal IT capabilities, without the need for large capital investment or a commitment to hiring full-time personnel. Companies of all sizes and industries are turning to outsourcing as a way to reallocate their resources from tasks that are "keeping the lights on" to initiatives that support key business objectives.
Despite the rising ransomware numbers and the numerous related headlines, many small and medium-sized businesses (SMBs) still don’t consider themselves at risk from cyberattacks. Nothing could be further from the truth. Smaller organizations are a prime target, and ransomware authors have only upped the ante in their methods to ensure they get paid. For example, many ransomware groups now threaten to expose or sell company data stolen in a breach if victims refuse to pay. In many cases, paying the ransom may be the most cost effective (and least publicly embarrassing) option. But what if your business can’t afford it? Or if the downtime from the attack is too much to recover from? And what’s the long-term psychological and emotional toll?
What is Zero Trust Security? Zero Trust Network Security is a security concept requiring all users to be authenticated, authorized, and continuously validates security configuration before granting or maintaining access to applications and data. Zero Trust security even requires users inside the organizations enterprise network to adhere to these authentications and authorization processes.
Cybersecurity and network security have proven to be critical during the pandemic of 2020. Healthcare industry sectors and providers have been pummeled by cyberattacks and data breaches. These cyberattacks have been documented for 2020 and have already, though September was seemingly the worst month for companies within the healthcare sectors.
In 2021, web security has become a priority for businesses across the globe. To test your website and infrastructures capabilities, it is best to perform a Vulnerability Assessment or a Penetration test. In the field, some refer to a ‘Penetration Test’ as pushing your infrastructure to its limits, looking for as many vulnerabilities as possible, while others may say that Penetration Tests are primarily focused on a specific target or set of targets.
Phishing campaigns are increasingly using some of the world's most famous technology brands in an attempt to trick victims. A report from Vade Secure has found that Microsoft, Facebook, and PayPal were among the most-impersonated brands in phishing scams during 2020 as hackers look to create ever more realistic fake emails.
Businesses’ online infrastructures are at risk more than ever in 2020 & 2021 as technology is further developed for hackers and online infiltrators. With these threats present, cybersecurity is paramount. Understanding, controlling, and managing risk mitigation to your company or organizations online assets is comprehensive, but Integrated Computer Services it here to make sure you company is prepared and safe.
Data exfiltration is a form of a security breach that occurs when data is copied, transferred, or retrieved from a server without authorization. The data can be sensitive information about customers and employees, financial or strategic information, product designs or intellectual property, or any data that could undermine an organization’s market competitiveness. When this data is purposefully leaked from the organization without permission, it is known as data exfiltration and when it is lost, the organization suffers a data breach.
Data protection and web security are making headway in 2020 into 2021 as companies and organizations become more aware of data, or network security breaches with advancing technology.
Whether you have a small VoIP phone system or a 300-line call center, VoIP implementation can come with it's fair share of issues. Here are 10 common VoIP problems and what to do about them.
Cybersecurity is something every business should pay attention to. Your organization's network connects your workers and serves as a way of communicating with the outside world. An attack on your network could ruin your business' reputation and potentially cost your company thousands of dollars. Outsourcing IT security provides peace of mind that your digital assets are protected. Network security is a complex field and one that needs specialist attention.
We have collected a list of the top 20 IT companies in New Jersey. We hope that this helps you find the right provider for your needs. Read on to connect with the right IT company for you.
WiFi networks present unique security challenges that can leave businesses vulnerable to hacks and data snooping. From your tax records, payroll, health information, data on your customers, even user logins and passwords can all be added up to extensive value if they fall into the wrong hands.
BYOD is a modern business acronym that stands for "bring your own device." Today, most employees use their own mobile devices or laptops for work to some extent. Creating a solid BYOD plan can save your organization from security nightmares. There's a lot of talk about what a good BYOD security policy includes.
Have you been considering using a MSP for your NJ law firm? A managed service provider offers a computing framework platform for the organizations to remotely manage their customer's IT infrastructure. The services may also extend to managing the end-user systems, basically on a proactive basis or under a subscription model. The MSP enables an organization to monitor servers, Exchange servers, firewalls, routers or switches, and Active Directory Servers from a centralized platform and location.
More than 40 percent of all cyberattacks are directed at small businesses, according to data published by Verizon. Now more than ever, small players can’t afford to have their core operations disrupted. Understanding the kinds of cyber threats out there is the first step to protecting yourself — and your company — against them.
Phishing and business-email-compromise (BEC) schemes are on the rise, causing losses in the $50,000 to $100,000 range to small businesses across the United States. More than a third of organizations said they received an email from someone pretending to be a senior manager or business partner.
IT professionals love office networks. They’re relatively easy to protect and control. These days though, with more and more people working from home due to the Corona Virus and the calls for social distancing to minimize health risks, digital security professionals face a whole constellation of new challenges, not the least of which is ensuring the security or the company’s network in the face of so many remote connections to it.
For most companies, remote work took place on a small scale. Then came the Coronavirus. It is a different world then it was three months ago.
The statistics are alarming. In any given year, nearly half of all small businesses may experience a cyber-attack or a data breach. Of those that are breached, 43% wind up going out of business immediately following the breach, and only six percent of companies survive beyond two years, post-breach.
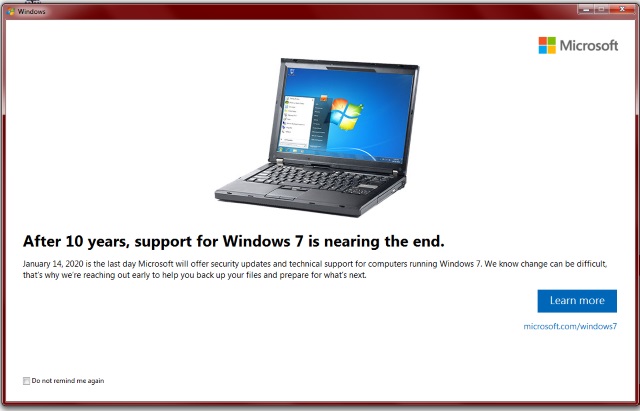
Security company Webroot published a report that revealed a sharp increase in the number of infections on systems running Windows 7. Checkout this blog article to learn why Windows 7 is becoming so risky.
There is a lot of information out there on what cybersecurity is, but the eventuality of it all is that someone somewhere is trying to get something. With enough effort, it is possible for anyone to get hacked, but there are somethings you can do to make it not worth the effort.
Right now, as you’re reading these words, do you know the state of your company’s network? How much capacity are you using? How smoothly are things running overall? Are there any bottlenecks that are causing hair-pulling frustrations for your employees?
Your employees are both your company’s greatest asset and its most glaring point of weakness, especially where information security is concerned. The unfortunate reality is that most people have terrible password habits.
If you’re relying on in-person visits by IT staff or specialists, you’re certainly paying too much for IT service when there’s an issue. If you’re looking for a quick and easy way to add to your bottom line, here are three ways that remote support service can help you do that.
What, exactly, is the cost of downtime, and what's the value of downtime prevention? When you look at the numbers and statistics behind the impact of downtime, you can see why it's so important to invest in downtime prevention to mitigate the effects of an IT systems outage.
If you own a small or medium-sized business, you may have heard the buzz. Microsoft Azure is changing the game. Unfortunately, that gets said about a lot of things, so you may have simply written it off as just another fad when you heard about it.
When your business data is at stake, having a strong antivirus system in place is key. Consider this one of the first lines of defense against nefarious programs and the people behind them. It's a wise investment in the safety, security, and reputation of your business.
Here at ICS, we love Microsoft Office 365 because the advantages of Office 365 are many. No matter what industry in which you work, we are certain that this technology suite can make a big difference in how you do business.
Many people these days are in the habit of making regular backups. That’s a very good thing, but how reliable are yours? When was the last time you tested them?
For companies running Windows 7, Server 2008 R2, or both, 2020 is going to be a year of big change. These businesses need to start preparations now. Windows 7 reaches its end of life in January 2020, which means that Microsoft will no longer support it or offer security updates, even for paid users.
In the earliest days of the internet, companies could get by with installing a good antivirus program and relying on their network firewall to run interference as needed and count themselves well protected.
If you haven’t yet made the leap to the cloud, it may be worth taking some time to consider why not. After all, cloud-based solutions offer tremendous opportunities and benefits to businesses of all shapes and sizes, but those benefits are especially compelling to small and medium-sized firms. Here’s a quick overview of what you’re missing out on.
The statistics are grim. According to a recent study, a staggering 61% of those surveyed said that their companies had experienced a cyber attack sometime in the preceding twelve months.
These days, businesses face a whole host of data security threats. Not only is the threat matrix constantly growing and evolving, but the attacks themselves continually grow in complexity and sophistication. Some threats are easier to manage than others. With a robust toolset, backed by round the clock monitoring and rapid response teams in place to deal with potential incursions, you can defend your company from all but the most determined threats.
Most business owners are aware that they should be backing their data up on a regular basis, but surprisingly there are still many that are not backing up. For those that do regular backups, only a small percentage ever bother to test their backups to make sure that everything is working the way it's supposed to.
In today's fast-paced, rapidly evolving business environment, SMBs can often struggle to maintain the complex technologies their businesses rely on. With resources stretched thin, it's all too easy to miss a critical update or fail to spot a looming security issue in a timely manner, and that can spell disaster.
Here are the five key advantages associated with utilizing Managed Services:
Cloud backup protects against ransomware by putting your files where the attacker can't touch them. But what if ransomware could hit your cloud storage? It could happen. A proof of concept called Ransomcloud has shown it's possible.
October is National Cyber Security Awareness Month, the perfect time to address the hidden risk of Shadow IT. If you aren't dealing with your Shadow IT problem, your business is not as secure as you think it is!
In this post, we'll discuss BEC attacks. We'll help you understand what BEC attacks are, educate you on the potential ways in which you might be compromised, and explain how you and your employees can reduce the risk that you'll fall victim to a BEC attack in the future.
When was the last time your business underwent a Network Assessment? As a business decision-maker, there are many moving parts to keep track of, and IT monitoring can easily fall through the cracks until something breaks.
Summer is winding down and open enrollment is right around the corner. Is it time for you to think about HIPAA IT compliance? Some companies are choosing to follow HIPAA regulations even if they are not covered entities or business associates. Do HIPAA regulations apply to your business? There are ways in which you may find yourself working with protected information.
Ransomware attacks are a serious threat to any size business. For a small business, a ransomware attack can even result in the company going out of business. Last year, ransomware was found to be the most prevalent form of malware connected to company data breaches.
The summer season has arrived! Warmer weather means families are spending time enjoying outdoor activities like hiking, bike rides, and beach days. With less time in the office comes more time on other devices, especially wearable technology like Apple Watches or FitBits. In other words, it is time to think about IoT security.
Passwords today are like spare keys that have been given out to too many friends and neighbors. Common password content like birthdays, favorite sports teams, or names of children or pets are easily found on social media accounts.
As an organization dedicated to providing comprehensive IT support to our customers, we try to notify our clients of vulnerabilities we uncover in our efforts toward the prevention of cybercrime. To protect your organization and its clients, please take note of the following security bulletin:
National Small Business Week is April 29 to May 5! According to the United States Small Business Administration, "more than half of Americans either own or work for a small business, and they create about two out of every three new jobs in the U.S. each year." You and other small and medium-sized business owners play a critical role in the American economy. That makes your network a prime target for hackers. This National Small Business Week, take a moment to reflect on the role technology plays in your company.
Mobile malware attacks skyrocketed last year. In just the first quarter of 2017, McAfee had already detected more than 1.5 million new incidents of malware specifically targeting mobile devices. By January of 2018, Google had removed 60 apps from its Play Store due to malware.
At times, it may be necessary to ensure that PCI-DSS compliance has been implemented in an environment. All businesses handing cardholder data, regardless of size, have to be fully compliant with strict security standards drawn up by the world's major credit card companies.
The terms backup and disaster recovery go hand in hand, but the truth is that backups are only one component of a comprehensive disaster recovery plan. When a company backs up its files, too often the belief is that employees can simply access those files, copy them back to their desktops, and be ready to get back to business.
Data security needs to be the main concern for all businesses in these times. Attacks are becoming more sophisticated and hitting major businesses at a more frequent rate. Even though you might be under the impression your business is insured for ALL cybercrime attacks through your current plan, you could be wrong.
-
Should your business move to the cloud? As more and more organizations make the switch, you're probably considering whether the change is a worthwhile expense
-
When your company's management wants to make a decision, does it do so without the relevant heads of marketing, finance, and operations at the table? Surely not!
-
Think you know how to create a solid, safe email password? Chances are, you're not following current best practices for email security. New standards were recently released by the National Institute of Science and Technology (NIST), and it calls for organizations to update their password-management policy to reflect the new recommendations.
-
In the wake of the massive Equifax security breach that was recently exposed, we wanted to take action to educate our clients about the breach and what's happening as a result of it. First, though, as part of this cyber awareness training brief, we want to take some time to review the specifics of what happened.
-
In 2014, Google announced that it was encouraging everyone to switch from HTTP to HTTPS, and made clear that doing so would have positive impact on a site's search engine ranking. Since then, more and more companies have completed this migration as part of their threat and vulnerability management strategies.
-
Before we go into detail about the latest threat we have been informed of, we need to urge all readers who use WebEx to upgrade to the latest version immediately! This week’s report hits close to home because attackers have found a way to reach victims through the popular online meeting software “WebEx”.
-
App ID theft has made its way into the picture just in time for holiday shopping and online purchases. In recent weeks there have been reports of Google Play and Apples App Store hosting phony versions of legitimate apps. These fake apps look identical to the real thing and have been causing problems for countless customers.
-
With today’s technology criminals are able to create malicious emails that look identical to the real thing. We suggest you question everything that comes through to your inbox. One click on a harmful link is capable of causing significant business distruption and financial loss.
-
We have found an uncommon phishing email which will hit your user’s inboxes soon. Many of the big service providers such as Google, Microsoft, Amazon, Twitter, PayPal etc. send out a security alert via email warning of a possible security-related activity such as “unusual sign-in activity”.
Similar emails have been used for password phishing for almost a decade, however, now these security alerts are being used as a new attack method for a technical support scam.
-
ICS makes it a priority to investigate the newest critical threats to your business network and as a partner we take pride in making sure your corporate network and critical data is secure.
-
As we have stated in previous blogs, email is the vehicle of most attacks. These emails contain attachment with .js, .DOC and other suspicious extensions. Once clicked, these extensions are capable of infecting business networks with malware, ransomware, Trojans, crypto locker and a wide array of harmful infections.
-
Security threats are constantly on the rise these days, if you follow the ICS blog you will know that there is a new scam released on a weekly basis. The frequency of these new threats make it difficult for updates and security patches to keep up. By the time antivirus vendors find ways to block theses malicious viruses, there has already been a new threat released.
All employees or individuals must be aware of the fact that even with the most cutting edge security software and hardware, it is still possible for the newest threats to slip through. When this happens it is crucial that employees are able to recognize threats and suspicions emails.
-
If you are a regular reader of the ICS blog you are no stranger to the amount of threats out there but for new readers we must stress the importance of security awareness. All these threats have the potential to cripple your critical business resources. We have been seeing an influx of phishing scams making their rounds lately and most have come via email. The newest wave have been including malicious attachments in the disguise of business related invoices or past due bills. These have been fairly successful because this method entices the targeted user to open the attachment without thinking twice. They automatically assume its business related and therefore legitimate. Once the attachment is clicked, malware or ransomware infects the computer. This week’s newest threat falls right into this category.
-
Yesterday, news broke that Prince Rogers Nelson was found dead in his home in Minneapolis at age 57. He was found unresponsive in an elevator and was declared dead shortly after. Internet criminals are going to exploit this celebrity death in a number of ways, so be careful with anything on anything related to Price's death: emails, attachments, any social media (especially Facebook), texts on your phone, anything. There will be a number of scams related to this, so think before you click!
-
Ransomware is advancing at an alarmingly fast pace. The main purpose of the ICS blog is to keep all of our partners, friends, and associates informed of all the latest threats. Awareness is a key defense tactic when it comes to the security of your critical business data. This week’s is a perfect example of how sophisticated the threats are becoming. In this ransomware attack the scammer actually knows the home address of the targeted victim.
-
Viruses and malware can create stress, especially in the business world where downtime equals loss of profits. It is very important to stay informed of all the latest threats in order to protect your data and with technology advancing at a rapid pace, malware programmers are finding different ways to sneak past network security features. This week’s threat is the perfect example of this. This new Trojan virus sneaks into your PC undetected and remains invisible.
-
Unless you have been living under a rock, you have heard all the rave about modern cloud technologies. Businesses all over the globe are now moving their data into the Cloud. In layman’s terms this means having your business data, website and email services on servers located offsite in a secure facility called a datacenter. Businesses can have their entire network in the cloud, or just segments of it. This depends on the individual benefits it can provide to your IT infrastructure. Although the general public has the correct idea about what the cloud really is, there are still a lot of misconceptions.
-
There are more malicious threats on the web than you can imagine, every minute a new scam is created or a new vulnerability is uncovered. These threats come in all shapes and sizes, just having antivirus is not enough anymore. The most important defense is you. The end user is at the forefront of their corporate network and the internet, and must be properly trained on safe practices. One of the purposes of our blogs is to make sure all of our friends and partners are aware of the new threats discovered on a regular basis.
-
Every week we are introduced to new threats, we cannot stress enough how important user awareness is in defense against these types of attacks. As soon as these threats are uncovered, another has already been created. These crimes advance with technology, and as we all know technology is advancing faster than ever. In phishing scams like this week’s, the attacker takes advantage of the most vulnerable aspect of any business computer network, the employees.
-
With all the advancements happening in technology every day, businesses have no choice but to dive in head first. Businesses that are not accepting to the changing tech landscape will be left behind in the blink of an eye. This is why it is very important to always be on high alert for scams and other malicious threats. The modern hacker ranges from someone working out of their parent’s basement to highly trained criminal organizations located all across the globe.
With this being said, businesses have the most to lose and often are the targets of the more sophisticated criminals. We have compiled a list below of the things attackers are looking for. Make sure these aspects of your business are kept under close watch.
-
Criminals will jump through hoops these days just to pull off a scam. Unfortunately, these ploys are becoming more advanced with the technological advancements in today’s world. Employees must be aware that there is always someone waiting for an opportunity to get their hands on your company’s business critical data. With this said, employees can never be too safe when questioning the validity of email senders and links to websites. With the wrong click it is possible to give these malicious programs access to your network. This year we have already seen our share of crypto locker, ransomware, and malware.
-
Everyone is interested in getting the best deal available, so when you hear you can get free or discounted Netflix you pay attention. In this instance, it was all part of an elaborate phishing scheme put forth to steal individuals personal data and infect their devices with malware. Being that Netflix is so popular, it offers a large platform and client database for scammers to work with. Reports claim that these attacks are complex and seem to mainly be initiated by the Eastern European Hacking group dubbed “cybermafia”.
-
WordPress is a very popular open source content management system. Open source means there are hundreds of people from all over the world working to make improvements to the platform and the source code is available to the public free of charge. WordPress is the most popular of its kind and is mainly used for blogging and content management. Recently these websites have been experiencing vulnerabilities that have been infecting user’s computers with Ransomware.
-
There is a new wave of phishing attempts that are more convincing than ever. You should always be cautious when anyone contacts you to notify you that they have found something wrong with your computer. Unless you are 100% sure that you know this individual, it’s a scam! Even if you think you know the person it could still be a scam, people can easily impersonate others and pretend to be someone they’re not. The scary fact about these types of phishing attempts is that the scammer actually provides you with the service tag of your computer.
-
Paying for services by the hour can be very costly, there’s no doubt about that. If your central air breaks, you call the AC repair company. If a drain gets clogged you call the plumber. When you get a computer virus, you call the IT technician. When something breaks it has to get fixed, especially if it’s slowing down business productivity. When it comes time to pay the bill, you will charged for every hour that was spent on your issue. Nine hours of labor equals a nine hour bill. This process is called time based billing, and it could end up costing your business an enormous amount of money that can be invested elsewhere.
More Info
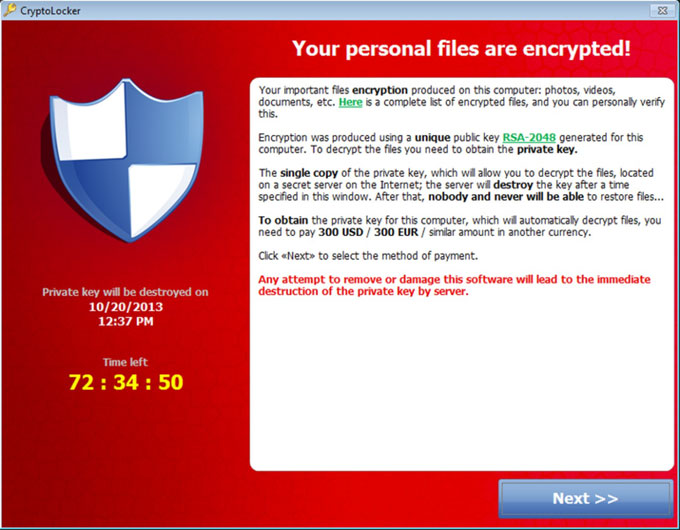
We are always reminding our partners and friends how important network security is. Even with all the latest security technology implemented in your network, the number one threat still exists, your employees. One of the biggest recent threats to your network this past year has been the ransomware called crypto-locker. This advanced threat will find its way into networks through mouse clicks from untrusted sources and attachments from unfamiliar senders. Once crypto-locker finds its way in, it encrypts all of the data on your network and holds it for ransom. Without current backups of your data if you don’t pay the ransom, you don’t get your data back. Sources say even the FBI suggests the safest thing to do for your data is to pay the fee.
More InfoIf you think staying with the same business technology you have been using for years is saving you money, think again! Not only is this slowing your business down, but if clients, partners, or customers find this information out, they will consider packing up their bags and taking their business elsewhere. Using outdated technology doesn’t only affect the productivity of your business, it affects your reputation.
More InfoIn this era hackers will try anything to steal your sensitive data, financial information and make you a victim of identity theft. Don’t think that the holiday season is a time when these criminals take a break to sip some egg nog. Instead these cyber criminals are scheming to use the holiday season as a way to steal from you through phishing emails and social engineering.
More InfoDisasters will arrive when you least expect it. These events can be natural or man-made and are very capable of causing prolonged downtime. A lot of businesses have DRP’s (disaster recovery plans) and think that is enough to keep them safe in the event of an emergency. A disaster recovery plan can be complex and include significant roles from a few to many employees in the office. It is very important that everyone involved knows their specific role and has walked through the process until they are comfortable with their responsibility. Below we have provided the basic steps your business should take in order to ensure that everything will go as planned in the face of disaster
More InfoIf you have owned or used a PC at work, chances are you have had to deal with at least one malware infection at some point. Besides being extremely annoying malware will slow down the flow of work and overall business productivity. Some infections are capable of slowing your computer down to a crawl and expose valuable company data. In this article we will discuss what you should do in the unfortunate event that your computer is hit with a malware infection.
More InfoData is the backbone of every business from enterprise to the SMB market. It’s imperative to make sure that your data is safe and available at all times. Disasters are capable of occurring without warning and can destroy all of your businesses critical data. Backups are necessary to ensure that no important data is lost during any type of disaster. We recommend having a professional backup and data restoration system implemented to ensure everything is available even during times of crisis. There are many different techniques when it comes to backups, below are just a few of the techniques used in today’s industry.
More InfoWe’re sure that everyone has been hearing all the buzz and excitement for the new Windows 10 upgrade and we are very excited and can’t wait to see what this advanced operating system can do to improve business productivity. Regardless of all the excitement and anticipation we suggest sitting tight and remaining patient during the initial roll out of Windows 10 free upgrade and urge our partners to wait before upgrading.
More InfoWe’re sure that everyone has been hearing all the buzz and excitement for the new Windows 10 upgrade and we are very excited and can’t wait to see what this advanced operating system can do to improve business productivity. Regardless of all the excitement and anticipation we suggest sitting tight and remaining patient during the initial roll out of Windows 10 free upgrade and urge our partners to wait before upgrading.
More Info
Most computer and internet users have had their computer infected with malware in the past. We have all heard of terms like trojans, worms, spyware, ransomware and viruses but what is the difference between them? In this article, I will explain each type of malware and how to protect your business critical data from these cyber threats.
More Info
Is your current Managed IT provider not cutting it for your business? Making the change to a new MSP can be a pretty daunting task, without the proper preparation that is. Integrated Computer Services has a guideline for all new partners. We make sure on boarding is done in a very organized and professional manner. This promotes a future of smooth sailing for your company. Below are some simple steps to address before transitioning to a new Managed IT Service Provider.
More Info
There is no company that can withstand long periods of downtime and large amounts of data loss ' the price some companies have to pay for this type of thing is bankruptcy. Top notch managed IT service providers work tirelessly to prevent or minimize data loss and downtime for its clients and end users and understanding your RPO (Recovery Point Objective) and RTO (Recovery Time Objective) is a critical piece to any good business continuity plan.
More Info
With all the new technologies available to businesses today, there is always the question of which is the best for your business. Traditional backups have always been the go to method for ensuring data protection and recovery. In the recent years the Business Continuity method is gaining popularity. Below we have listed some of the main differences between the two methods in order to help explain why the business continuity is gaining momentum in the tech community.
More Info
If you are not a trained professional in the IT field, making technical decisions can be overwhelming. A reputable Managed Service Provider can offer expert consulting for all your IT needs. For that reason, Integrated Computer Services has a staff of highly trained and experienced technicians that are specialized in working with all types of hardware, software and networks.
Over the years ICS has witnessed our fair share of avoidable mishaps when it comes to clients making important network decisions without proper advisement. We strongly recommend that our partners run everything by network administrators before implementing any changes or purchasing new technology. In the business world money has gone to waste on behalf of poor technical decisions made by people who didn't exactly know what they were doing.
More Info
Microsoft Windows 2003 will stop receiving support starting July 14th, 2015. This is the final critical reminder we are sending out about Microsoft Server 2003's end of support life. This is essential for users to be aware of, if you are currently running critical line of business applications on Windows Server 2003 you will need to start taking the necessary steps toward upgrading as soon as possible! With the end of support life come a VERY high risk for network intrusion and potential threat. This is because "end of support life" means that there will be no more updates or security patches released to combat the new vulnerabilities as they are discovered. This leaves your network defenseless against these threats. Businesses who choose to continue to run Microsoft Server 2003 are putting their company IT infrastructure at high risk.
More Info
Search engine optimization is a critical part of every successful business. This service will help increase legitimate internet traffic to you company's website. ICS offers expert search engine marketing services that will bring your business "organic" search engine results. Research has proven that over 70% of search clicks are being done via organic results, this makes search engine optimization a critical marketing tool in today's highly competitive business world! This service will boost your web traffic, search engine rankings, and conversions for your clientele.
More Info
Integrated Computer Services is an industry leader when it comes to managed services, and we have the credentials to back it up! We regularly ask our readers to go back and see how their technology partner compares to us. In order for an MSP to be qualified to support business networks with advanced IT infrastructure there are a several certifications and affiliations that are essential. If your MSP or technology partner is lacking in this department, you should seriously consider switching to a new technology partner who is more qualified to securely manage, maintain, and deploy network architecture for small, medium and enterprise business.
More Info
With today's advances in technology it is not necessary or cost effective to have a fully staffed in-house IT department for small and medium sized businesses. Technicians now have the ability to remotely access anything from printers, computers, switches, routers, cameras, vendor equipment and basically anything that has the ability to reach the internet. For small to medium sized businesses it is not economically feasible to have to pay for the presences off a fully staffed IT department when there are managed service providers like Integrated Computer Services that do it all from their headquarters.
More Info
If you own a desktop PC you have thought about this question on more than one occasion. Growing up we were exposed to computers for the first time, one of the earliest task we learned was powering up and shutting down the PC. Were you ever instructed to power down your computer every night with the given impression that this will somehow miraculously make the life of my computer last longer?
More Info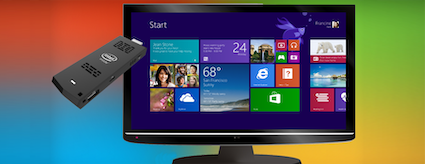
With all the fast paced advancements happening in the technology field it's getting very difficult to think of what will be available to businesses next. It is our pleasure to introduce you to the new Intel Compute Stick. This handy micro device gives mobile business professionals the capability of transforming a TV with an HDMI port into a fully functioning computer running Microsoft Windows 8.1 .
More Info
We are happy to inform everyone about the upcoming release of the Windows 10 Operating System! This upcoming version will succeed the current 8.1 version and offer many advancements and new features. Microsoft has been able to enhance the capabilities of the Windows 8.1 in order to produce the most efficient and business critical OS on the market. If you are currently running Windows 8.1 this new release is something to get excited about, especially because there will be a free upgrade offer. That's right, Microsoft will be offering free upgrades to all the people who are currently running Windows 8.1! With this new operating system Microsoft has worked out all the flaws and shortcoming of the 8.1 version, and the improvements will be very noticeable. One new exciting feature that has everyone talking will be the addition of a virtual guide named Cortana. Take a seat Siri, you might have some competition! This new business savvy operating system is the future. Get acquainted, because you will definitely be seeing a lot of Windows 10!
More Info
Integrated Computer Services is always encouraging our partners to be technologically strategic. This means that your business is open to accepting and embracing modern technology. Technologically strategic businesses leverage cutting edge technology to gain a competitive advantage in their industry. VoIP (voice over IP) phone systems are the latest and most advanced phone systems taking over the business world. If this is a service you haven't heard of, we strongly suggest you give it some consideration in order to optimize your telecommunication services. More and more businesses are making the switch to VoIP phone systems, don't be left behind.
More Info
Glen Rock, New Jersey 03/17/15 ' Integrated Computer Services, Inc. announced today it has received the CompTIA Managed Services Trustmark', a respected industry credential that signifies its adherence to best practices for technology service delivery and customer interaction. CompTIA is and has been one of most respected and trusted names in the IT industry for years. With that said it is a standard for every legitimate MSP and IT outsourcer to utilize CompTIA's information while following their suggested standards and best practices. CompTIA is best known for their in depth knowledge and contributions to the industry and service expectations.
More Info
Integrated Computer Services is very familiar with ITIL's service life cycle approach. These are effective steps that we utilize in order to ensure that we are providing our clients with the best support possible. ITIL's approach consists of five steps that every IT company should follow. These five stages consist of service strategy, service design, service transition, service operation, and continual service improvement. We suggest you become familiar with the following five categories and evaluate your current managed service provider. Has your current IT utilized any of these techniques? If you had to answer no, then you should re-evaluate your current MSP. In order to manage networks successfully these five steps must be practiced and utilized for every business.
More Info
There all different types of businesses out there, all having different strengths, weaknesses, wants and needs. But one thing is certain, technology is present in every business, office, cubical, and meeting! Technology is everywhere. Although technology is a part of all businesses, it serves a unique role in each. Most businesses will generally fall under one of three categories when it comes to their technical needs. Companies can be either technology strategic, dependent or adverse. Take a look and find what category your company can relate to.
More Info
Integrated Computer Services has been built on essential core values that have been ingrained into the company throughout our 12+ years of service. We take pride in practicing what we preach and have a strict set of core values that every employee takes pride in following on a day to day basis. These values ensure that your company's information technology is in the best hands possible. If you are not currently an ICS partner we suggest you evaluate your current IT solutions and compare how they stand up against Integrated Computer Services. If your current partner is not displaying the same quality of service and value that ICS has to offer, we urge you to reevaluate your situation. Top notch IT services is not only about being responsive to issues as they occur, the other half of the battle is being proactive to ensure that you will not have these problems to begin with as well as keeping your company up to date on the latest technology.
More Info
There is nothing more important to the well-being of a business than the security and reliability of its information systems. If your company has a flawless Disaster Recovery Plan you will be able to rest easy knowing no matter what happens you will not lose any of your businesses critical data. Without a good "DR" plan, a simple act of nature or a man-made incident could lead to permanent data loss and prolonged downtime.
More Info
Internet use policies are one of the most important aspects of your organization's networks security. These policies allow work related websites to be accessed by employees, and harmful or distracting websites to be prohibited and blocked. Internet Use Policies will increase company productivity plus reduce unnecessary risk of malware, viruses and hackers. Once you have a policy in place you will need a content filter service or web filter device to enforce the policy.
More Info
We would like to introduce you to the new Surface Pro 3, which is a new business focused tablet-PC designed by Microsoft. We believe this tablet is a game changer for the mobile business professional since it can replace your laptop while still functioning as a convenient tablet-pc. The Surface Pro 3 includes the full version of Window 8.1 Professional allowing you to run all of your line of business applications including the full version of Microsoft Office 2013. Need to type fast and efficiently on the go? Road warriors can get the optional Bluetooth keyboard and mouse to boost productivity while on the go.
More Info
This day in age the average user is using more than one device on a regular basis. With the increase in cloud technology users are able to access all there business critical data from all over the globe. Individuals will be logging their credentials into numerous applications and services provided over the internet. The increasing capabilities of cloud technologies does not come without significant risk. It is very important to the security of your network and business data that all users have a strict regimen to follow when it comes to creating and regularly changing their passwords. With all the technology we have in this day in age, the security of business networks are still in need of improvement. Time and time again we hear about these security breaches within large enterprises. There are many different pieces to the security puzzle of a network, and secure passwords are your first line of defense. Below are just a few tips and recommendations when it comes to managing the password criteria for your network's users.
More Info
Integrated Computer Services offers unlimited support packages suitable for businesses of all sizes and types. We ensure your business is always running at top speeds and you will always be available for the needs of your clients. We watch over your entire network and cater to its needs so you don't have to. This enables you to spend more time and energy on improving and growing your business, without having to worry about your network and issues with decreased productivity. We offer a wide arrange of affordable and efficient network solutions. Integrated Computer Services will provide top of the line support at a more affordable rate than an in house IT technician.
More Info
In order to keep your business up to date with all the best and most reliable technology we have come up with the 4 year rule. This is rule states that any hardware, server, laptop, workstation, or software that is four or more years old should be under serious consideration for replacement. Technology is constantly improving at a fast paced rate and within four years it's more than likely this equipment has been surpassed by technology that is much more advanced. Your company might be able to stay afloat with the older outdated hardware and software, but chances are your competition will be running more efficiently with newer technologies. Working off of hardware and software older than four years can also be a potential risk to your business. This risk of equipment crashing becomes a lot greater the older it gets, this brings the risk of more frequent downtime and less productivity.
More Info
Recently there has been a growing trend of individuals falsely posing as Microsoft technicians in order to retrieve sensitive information from end users. It is very important for you to know that Microsoft tech support will never call you out of the blue, in order for a Microsoft technician to call you a support ticket must have been created on your end first. These individuals are very tech savvy and are very familiar with the ins and outs of how Microsoft and their support team work. This makes it more difficult to decipher whether the phone call is legitimate or phony! In recent reports Microsoft claims to have received as many as 65,000 complaints from customers who have been targeted by fraudulent Microsoft technicians. Legitimate companies have also been penalized for unrightfully using the Microsoft trademarks and logos for their services. This is illegal in every sense, and these companies are trying to affiliate themselves with this technology powerhouse in order to boost their appearance and credibility for their clients.
More Info
The internet can be a dangerous place when it comes to potential threats to your businesses computers and network. The uniformed end user is capable of unknowingly opening the door for viruses, malware, and threats that will slow down your network causing potential downtime. These threats can be disguised very well so it is important to be alert and on watch for anything suspicious or illegitimate looking. Sometimes these threats will look very real and be disguised as an advertisement or an email from a large company you are familiar with. Always be observant and question anything that might look a little odd.
More Info
The security of your network should be one of your business's biggest concerns. Your data is very important, and there are always individuals out there who will be able to benefit from stealing it. We have plenty of experience in supporting businesses, and the most common types of security breaches that we have heard or witnessed could have been easily prevented.
More Info
When technical issue arise we are aware that they can bring business productivity to a halt. We would like to make the support request process as easy and expedient as possible. Below is a description of the two best ways you can submit a support request when technical issues arise.
More Info
"The Cloud" is the official buzz word being used these days to describe hosted services. Hosted services is not a new concept, this has been in the IT industry for the past 15-20 years. In recent years this trend has been picking up a lot of momentum due to larger companies like Microsoft offering these services to large scale businesses.
More Info
Your business's data is the heart and soul of your organization, without it your business is dead in the water. In order to be fully prepared for any potential problems that may arise, it is critical that your business has a rock solid backup and disaster recovery plan implemented. With a fool proof plan instated you will be able to breeze through your workdays without having to be concerned with important information and software being permanently lost.
More Info
Being a Managed Service Provider, we know viruses and malware, it's what we do. So for us, it's obvious pretty quickly that there is something living in your PC that shouldn't be there. Unfortunately, end users don't have the years of experience we do in finding the warning signs. Here are a few tips to help you identify that something isn't quite right and should give our support team a call.
More Info
It has come to our attention that Microsoft has been performing random licensing audits on businesses using Microsoft software products. It is essential to your company that you have the proper number of licenses for the number of users. If your business is found to be lacking the correct number of licenses you will be facing a possible lawsuit or penalty.
More Info
If you're like the rest of us, sometimes the influx of emails that flow into your inbox could become a little overwhelming. Below are just a few simple tips to help keep your emails from piling up to an unmanageable amount!
More Info
In this day and age you can never be too careful when it comes to protecting your personal information. With today's technology there are numerous ways in which the modern criminal will attempt to fool you into forfeiting valuable information. Phishing is when individuals try to scam innocent people by sending them emails claiming to be legitimate businesses.
More Info
When talking about hacking, most people picture someone hunched over a computer as lines and lines of Matrix-esque code scrolls across the screen. However, when speaking about hacking attacks in regards to Social Engineering this couldn't be further from the truth.
When employing Social engineering the attacker uses human interaction and social skills to obtain or compromise information about a company. These attacks typically take the form of emails, websites, phone calls, or sometimes may even be carried out in person. They are typically after data such as usernames and password, credit card or account information, and much more.
More Info
When talking about hacking, most people picture someone hunched over a computer as lines and lines of Matrix-esque code scrolls across the screen. However, when speaking about hacking attacks in regards to Social Engineering this couldn't be further from the truth.
Microsoft Corporation will cease to support Windows 2003 server starting July 14th, 2015. In other word, when this date arrives this server operating system will no longer receive critical updates or security patches. The only way to receive continued support for these servers would be through customer support agreements.
More Info
When it comes to the battery life of our hand-held devices, we will never be satisfied. Everyone has experienced the hardships of a dying battery on a portable device at one point or another. There are a few preventative steps that you are able to take in order to keep your device alive for longer periods of time. Below are just a few simple steps you can take in order to maximize your devices battery life.
More Info
Integrated computer Services offers unsurpassed IT services all throughout the NJ and NY area. We offer top of the line technical support all within the budget of your business. Integrated Computer Services manages businesses of all different sizes. We make sure that all critical systems are running efficiently 24/7 and our technicians are well versed on all the latest technologies in the field. We ensure that your network is always in good hands, allowing our clients to focus on the needs of their business.
More Info
Are you considering hiring a Managed Service Provider? Maybe your information technology infrastructure is 5 years old or your business technology platform cannot keep up with your growing business needs. Below is a list of 4 reasons why you need to hire an MSP (Managed Service Provider) as soon as possible.
More Info
Nobody likes waiting for support (even its only a few minutes) and sometimes contacting your IT provider and waiting for a technician's assistance may not even be necessary. Here are some quick and easy tips to keep things running smooth and prevent some of those unnecessary calls to the support help desk.
More Info
While software and hardware security solutions can protect users from most malicious content, there is no 100% fool proof solution. This is why it is becoming increasingly more important to train your end users to browse and email smart and safely. Here are some tips to make sure your employee's are browsing and emailing with your company's safety in mind.
More Info
The Cryptolocker virus that has been making it past some spam filters and destroying companies' files shares and file servers. Cryptolocker usually sneaks into your network by email attachment. The Cryptolocker virus is disguised in an email referencing a fax, delivery or shipment in the subject line. It is very important that if you get an email in with an attachment and you are not certain that you know who it is from, do not open it! Right click on the email and send it to junk mail, block the sender, and permanently delete the email by holding the shift key down and then right click to delete the message.
More Info
I'm sure you are all aware of how important your email system is to the productivity of your business, the average employee spends a significant part of their workday using this tool in order to pass information between employees, clients, and the rest of the world. It's hard to remember how work was before this messaging system made like a little bit easier for all of us. Just like everything else, as time progresses so does technology. Over the years emailing systems have advanced and made communications between us a lot more convenient.
More Info-
Download our brochure to learn more about us
Download our company overview for more information about us
Download Brochure
About Us:
- Microsoft Silver Certified Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated