IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Please be aware of the following phishing techniques designed to get full control of your email mailbox.
Initially, a legitimate message is sent to you by a vendor, client, co-worker, or Microsoft:
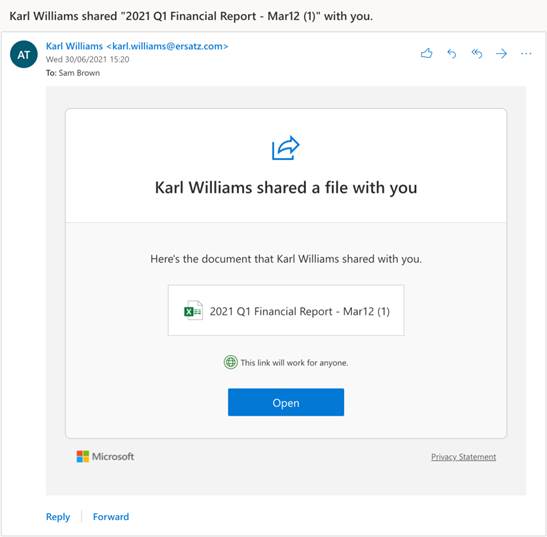
Maybe you’ve been waiting for the latest financials or you suspect this was sent erroneously but you’re curious and want to take a peek. When you click the link you are presented with a prompt that looks just like the “Yes give me access” prompt you’ve clicked through a thousand times. It's a microsoftonline.com domain, it's also HTTPS, and there’s a green tick in the corner- so everything looks fine.
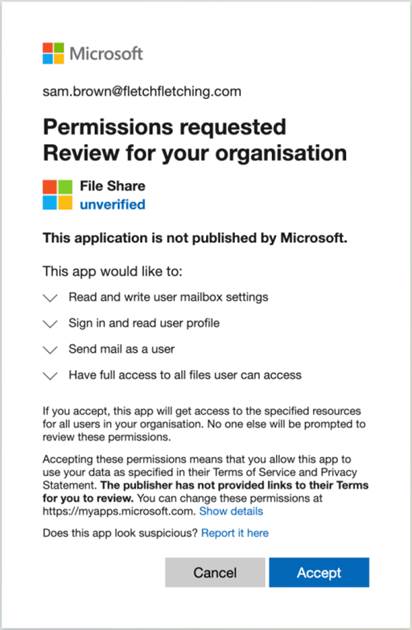
Would you click accept? Most likely, yes. Our muscle memory is in full control and we click “Accept” before even glancing at the screen.
However, If you look closely, you may have noticed that this was asking you to approve access rather than granting you access.
And just like that- you’ve been consent phished. You’ve just granted the attackers permanent access to your account, which they retain even if you change your password or have MFA enabled. Chances are the attacker’s tools will immediately start downloading every piece of data you just granted them access to, which they can then explore at their leisure.
By clicking “Accept” you would have granted some pretty serious permissions:
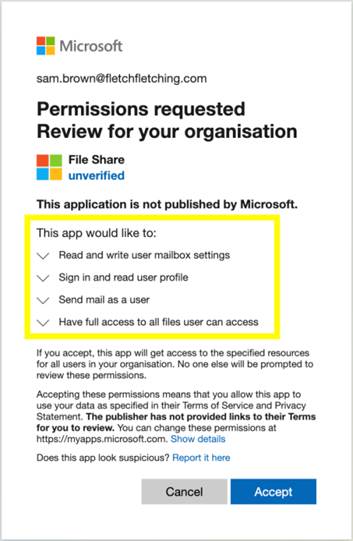
These permissions allow the attackers to read and write any files you have access to - they could download all the emails\files and then delete the originals.
The attackers also got permission to send emails as you. They could send emails to your colleagues and phish them too. (That wouldn’t be an impersonation email, where the email “looks” like it came from you- the email DID come from you!)
Lastly, the attackers asked for permission to manipulate your Outlook settings, with this they could set up a mail forwarding rule so that they get copies of all your new emails forwarded to them directly
Consent phishing is still an emerging technique that has not reached peak usage by attackers yet.
Please remain alert to all incoming emails, and read everything before clicking accept. Likewise, you may want to verify with the sender via a phone call that they actually sent a file\message to you before you take any actions on the request.
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Silver Certified Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






