IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Due in large part to COVID-19 and the increased prevalence of remote work, ransomware attacks dominated 2020, and experts predict there will be at least twice as many cases of data theft in the 2021.
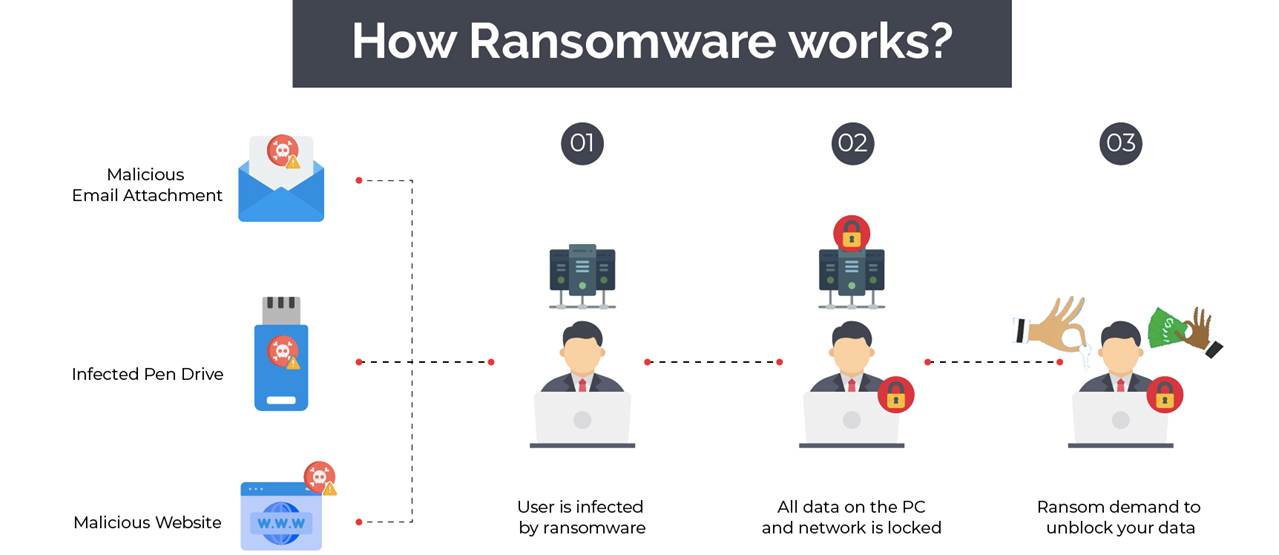
The U.S. Cybersecurity & Infrastructure Security Agency defines ransomware as “a type of malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid.” It often spreads through phishing emails or when a person inadvertently visits a compromised website.
How Does a Ransomware Attack Work?
In order to become victim to a cyber-attack, you must first allow criminals access to your computer system or network. Of course, you don’t “allow” access on purpose, but criminals will access your system through a “vector,” some of which include:
-
Email attachments
-
Social media messages (example: Facebook friend requests)
-
Pop-ups
These attachments and messages are designed to look real, of course, so that you’ll click on them, which allows criminals access to your files and information. Once you do so, however, the ransomware will encrypt your files.
The attacker then typically demands a ransom from the victim to restore access to the data upon payment. Users are often shown instructions for how to pay a fee to get the decryption key. The costs can range from a few hundred dollars to thousands, often payable to cybercriminals in Bitcoin.
Effective ways to combat ransomware attacks
Network security is critical for any company today, especially when we live in an age where data is an organization’s most valuable resource. But protection does not come cheap. Effective network security is not just about tools and technological solutions; it is paramount to develop careful strategies tailored to the company’s operations and risks. Some of the most useful network security tactics have been explained below.
Risk Assessment
This is the first step. Every organization needs to take proper inventory of its assets as well as analyze and document vulnerabilities associated with every piece of equipment. Beyond equipment and facilities though, modern network security is intricately tied to data protection. Therefore, a proper risk assessment should be concerned with data and information collection and storage, access and authentication protocols and endpoint security. That is, the questions that must be asked include:
- What kind of data and information do we collect/store?
- How important is this data?
- How is the data stored?
- Who can access the data?
Creating a Resilient Cybersecurity Culture
People, not devices and endpoints, are the most vulnerable part of the cybersecurity structure. No matter the network security apparatus in place, it all falls apart if the employees are not in tune with cybersecurity best practices. There is not much that policies can achieve if a proper cybersecurity culture is not ingrained in the organization and its employees.
This goes beyond regular cybersecurity awareness training, although that certainly matters. It is about fostering consistent security practices that actively limit employees’ (and thus, the organization’s) exposure to data breaches. That is, every employee (whether working remotely or on-site) has fully integrated cybersecurity considerations into every action they take.
It in increasingly common for IT auditors to ask if employees are aware of and annually review the Company IT policies. Regardless of the answer, the next question is: ‘are employees disciplined and\or terminated for not following IT policies.’
Network Threat Detection
Remember that network security should not be limited to defense. One primary reason for this is the increasing spate of zero-day attacks. Organizations should be actively hunting down threats. A network can remain breached for several days while the attacker continues to perform exploits in the background, remaining completely hidden from the information security team/department.
This is where the importance of visibility comes in. IT Security teams should be able to monitor network traffic at all times, flagging down suspicious movements, especially naive actions taken by employees that may expose an endpoint. This requires the use of advanced security tools (including artificial intelligence and machine learning) to monitor the network in real-time. The ICS 24/7 Security Operations Center conducts such investigations and eliminates threats before hackers or ransomware can damage the network. Contact ICS today for more information on Endpoint Detection and Response.
Next Steps
The Cybersecurity & Infrastructure Security Agency lists a variety of best practices to protect you and your company against ransomware, such as being suspicious of all emails and avoiding clicking on links or opening attachments within them
At the end of the day, ransomware attacks will never go away, especially as criminals incorporate new techniques and adapt to new technologies. But there are security best practices and steps you can take to protect your business or organization and help ensure that you aren’t the next victim of ransomware.
Contact ICS today to determine what security enhancements are needed for your specific organization
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Silver Certified Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






