IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Ransomware is one of the biggest cybersecurity threats to businesses today, and cybercriminals can potentially make millions of dollars in a single successful attack.
Now, cybersecurity researchers have discovered a ransomware campaign asking employees to install ransomware on their organization’s network, in return for a slice of the payout.
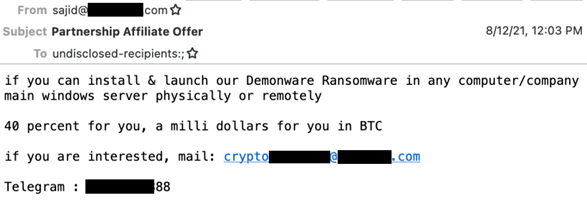
Analysis of the files sent by the attacker indicated that they're distributing a version of “DemonWare” ransomware, which is freely available to download from GitHub. Its original author placed it there to demonstrate how easy it is to make ransomware.
Finding Targets through Social Networks
When analyzing social engineering, one of the biggest questions is ‘how did an actor initially get the target’s contact information?’ In this case, the attacker revealed he collects his targeting information from LinkedIn, which, in addition to other commercial services that sell access to similar data, is a common method scammers use to obtain contact information for employees. Then, he simply messages them with the offer.
Concluding Remarks
Cyberattackers are relentless in looking for weaknesses to exploit- including in humans. Experienced ransomware operations benefit from finding insiders to help them gain access to networks. LockBit ransomware – which has surged in popularity in recent months – regularly advertises for insiders to help carry out ransomware.
To prevent the network from being compromised with ransomware – be it via an outside intrusion or an insider threat – ICS recommends Blackpoint Security. Other cybersecurity products on the market today lack the most important capability: real-time threat response. The reality is that attackers will find a way to breach a network no matter how many preventative measures are put in place, as the ransomware “invitation” above illustrates. When the attacker bypasses the defenses, tools must already be in place to put an end to the attack before mayhem occurs. Blackpoint provides such threat response: detaining infected devices instantly, kicking the hacker off the company network and saving critical assets.
Stop CYBER Threats in Real-time with Built-in, Immediate, and Effective Threat Response

Schedule a Demo Now
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Silver Certified Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






