IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Most people are familiar with ransomware. We’ve read news stories detailing the computer plague that has been targeting industries for the past few decades as well as the high-profile ransomware attacks against large organizations in these last few months. And the truth is, that big or small, we are all a target. Ransomware targets data- regardless of who owns it, where it is located, or what it is used for. Ransomware is also becoming more capable. In particular, ransomware writers are aware that backups are an effective defense and are modifying their malware to track down and eliminate the backups.
Backups Can Be Infected Too
Over time, ransomware has evolved from the low-level effort of deploying malware to open networks to more sinister and calculated attacks launched by individuals who want to guarantee their hard work pays off. Attackers have elevated their scope and tactics to take over backup solutions before they trigger the ransomware campaign. This more aggressive methodology impairs recovery processes and aims to remove a victim’s alternatives to paying up.
A network that is infected with ransomware will have all of its data encrypted with a password known only to the attackers. This blocks your company staff from being able to access their files, application data, etc. Ransomware starts by infecting one machine, and then spreads through the network until it has encrypted information across all devices. This attack will also encrypt the BDR unit that your organization uses. These BDR systems are always online and accessible and thus are susceptible to having the system backups encrypted by the ransomware. (File-level backups are not affected)
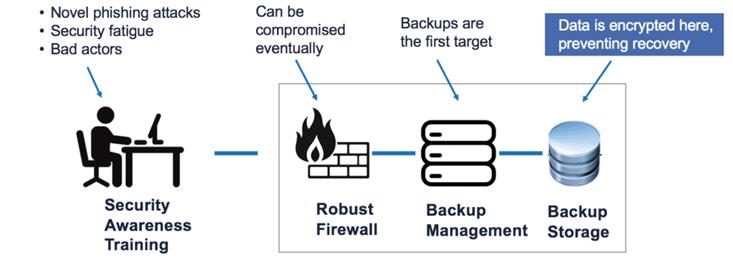
Protecting Backups From Ransomware
First and foremost, security is most effective when implemented in layers. The ICS security stack involves several preventative layers of defense, such as inbound spam\malware filtering, endpoint protection via AntiVirus with malicious code scanning, multi-factor authentication, user awareness email training, Windows Group policies, and other security products\services.
Current Risk to Your Organization
As a last resort, backups help your company recover from data loss caused by ransomware attacks. However, in a ransomware scenario, your organization's BDR unit is at risk of being infected- thus removing the capability of restoring system\file data from backups! Thinking about a ransomware attack on your network, how would you answer these questions:
- Can our business wait weeks or months for our network infrastructure to be rebuilt?
- Can our business unexpectedly purchase tens of thousands of dollars of equipment necessary to rebuild our network?
Solution: Isolate the Backups
The more barriers there are between an infected system and its backups, the harder it will be for the ransomware to get to it. In fact, with the ICS ‘cold storage’ solution at least one full image copy of all servers on your network are stored in an offline repository. This offline repository is completely inaccessible from the network. Thus, if your organization is attacked by ransomware that also seeks to destroy backups, the ransomware will be unable to access the ‘cold storage’ copy. (For technical details on how cold storage is accomplished, please speak with an ICS Backup & Recovery Specialist.)
Rather than waiting weeks or months, with the ICS ‘cold storage’ solution, your organization can return to normal within 24-48 hours following a ransomware attack:
- The ICS Security team will clean the network of the ransomware, and identify\close the point(s) of entry.
- The ICS Backup & Recovery Team will use the cold storage of the servers to restore them to a point in time before the ransomware encrypted the data.
 Take Proactive Steps to Reduce Risk
Take Proactive Steps to Reduce Risk
Please see the attached quote, which is a one-time charge, to get this cold storage solution for your organization. After purchase and installation of the materials required, any additional configuration and maintenance is covered by your existing contract with ICS.
Please also let ICS know if you would like more information on preventative security solutions, such as Multifactor Authentication for Windows Login, or any other solutions to secure your organization.
About Us:
- 150+ 5-Star Google Rated IT Firm
- Microsoft Silver Certified Partner
- SOC II Certified Managed Service Provider
- Better Business Bureau A+ Rated






