IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Network Security Threats
 Examining the relationship between the equipment used for devices to
communicate with each other and how data is transported both fall under the umbrella of network infrastructure
design and network security threats.
Examining the relationship between the equipment used for devices to
communicate with each other and how data is transported both fall under the umbrella of network infrastructure
design and network security threats.
Managed Switches/VLAN
A network switch passes along data to the intended device within an organization?s network. They connect multiple PC?s, servers, printers, and any other network devices so that each can send and receive communication from one another. The more devices that get added to the network, the more work is required by the switch to make sure the data is being passed along to the specified recipient. However, as a SMB grows larger, this underlying piece of equipment becomes increasingly important, not just from a productivity\speed standpoint, but regarding network security threats as well.
Typically, the network switch used in a SMB environment is an unmanaged switch. This means it works right out of the box without the need for any configuration and allows unrestricted communication between devices. A switch that supports a range of advanced features is called a managed switch. One such advanced feature is the ability to create a Virtual Local Area Network, or VLAN.
A virtual local area network is a set of devices that are grouped together to create a single and isolated domain (environment) segmented from other devices on the network.
When a machine becomes compromised and there is no VLAN isolation, the compromised machine is used to try to gain access and infect all other machines on the network. However, with VLAN, the compromised machine is isolated so that it will only be able to communicate with other machines in the same VLAN (group), thus reducing the level of impact of network security threats. The same will apply to a disgruntled employee. The machine they are on can only attempt access to other machines in the same VLAN, thereby limiting potential damage.
With VLAN implementation:
- Departments within organization can be given their own VLAN to communicate and share data only between themselves, thus limiting potential network security threats.
- Guests can be allowed access to the Internet without being given the ability to access the server and other devices on the network.
- Content Filter addresses safety, security and productivity concerns by providing the controls to implement Internet-use policies, and block access to inappropriate, unproductive or illegal web content.
- Real-time gateway anti-virus engine that scans for viruses, worms, Trojans and other common online network security threats
- Dynamic spyware protection blocks the installation of malicious spyware and disrupts existing spyware communications.
- Powerful intrusion prevention protects against an array of network security threats such as worms, Trojans and other malicious code by scanning all network traffic for malicious or anomalous patterns.
- Multi-engine sandbox to prevent unknown threats such as zero-day attacks and ransomware.
In addition to the isolation aspect of VLANs, there are many other organizational benefits of managed switches for networks with a sizeable amount of devices, including improved network efficiency.
Unified Threat Management
Unified threat management (UTM) is an information security term that refers to a network security device that combines multiple security functions such as a router, firewall, and other features (Kapersky, 2014). The SonicWALL UTM device includes the ability to enable advanced security features that keep network security threats at bay while eliminating the complexity typically required to setup such services. A SonicWALL branded UTM can be considered a complete security solution for a SMB network as it provides:
The unique multi-engine sandbox feature adds an additional layer of protection against network security threats that seek to avoid detection, and stops these threats before they even have the chance to enter the network. Suspicious code and files are sent to the SonicWALL Capture cloud service for analysis. The code or files are run, and its behavior is analyzed to determine if the code or file is safe, or attempting to perform malicious activity. If the files are malicious, they are blocked and not permitted to be downloaded by any workstation on any SonicWALL network around the world.
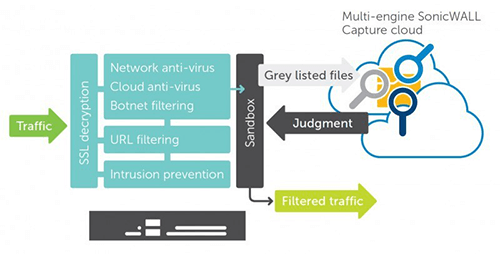 Figure 5: As data (traffic) flows into the
network, the SonicWALL UTM device scans and filters it so that only safe and approved
content is delivered to the endpoints.
Figure 5: As data (traffic) flows into the
network, the SonicWALL UTM device scans and filters it so that only safe and approved
content is delivered to the endpoints.Network security threats aren?t going away anytime soon. Devices like these will keep your data safe and business ahead of the game. Contact us today for a free assessment.
Kaspersky. (2014). What is Unified Threat Management (UTM)? Retrieved from Kaspersky: https://usa.kaspersky.com/resource-center/definitions/utm


