IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Network Management Services & Solutions
 The ever increasing number of data threats to businesses compels
organizations to develop a risk
management procedure to deal with the fallout of the unexpected. However, even before
that time comes, consideration must be given in how to prevent such things in the first place.
This process of doing so is called network hardening, and should be included in all network
management services. With the proper mindset and procedures in place, the probability of such
things as data breaches, unauthorized system access, and compromised machines can be greatly
reduced. Aspects of hardening the network include physical security, network security, and host
(or end-point) security.
The ever increasing number of data threats to businesses compels
organizations to develop a risk
management procedure to deal with the fallout of the unexpected. However, even before
that time comes, consideration must be given in how to prevent such things in the first place.
This process of doing so is called network hardening, and should be included in all network
management services. With the proper mindset and procedures in place, the probability of such
things as data breaches, unauthorized system access, and compromised machines can be greatly
reduced. Aspects of hardening the network include physical security, network security, and host
(or end-point) security.
Architecture and Delegation
In the recent past, almost all organizations considered data security to be in the last stage of an IT project. Some even waited until after the network or application was designed and deployed before addressing these network management services and concerns. That approach is no longer viable in today's world, where within moments of being connected to the internet, a hacker can find, target, and exploit any system weakness. Additionally, organizations have found that it takes much more effort and capital to address data security concerns if pushed off until after deployment.
When the SMB environment is examined, several solutions and network management services are available to secure existing systems from common threats. Some are automated, meaning that protection takes place in the background, while other solutions require a change in mindset of the organization's employees. For example, an employee must be trained to recognize phishing emails, not reuse the same password on multiple platforms, and other common mistakes like these.
Principle of Least Privilege
Network management resources should only be made available to persons who have a legitimate need to use, view, or modify them. However, more granular controls are necessary. For example, in a physical sense, a key may be given to an employee to access the front door of the building, but not a key that opens the CEO or President's office door. That employee is only given access to something the organization deems necessary for their function within the company. From a network security perspective, something similar must be accomplished.
In the SMB environment, user access is sometimes ignored until it is too late. For example, an owner of an SMB may compile an excel spreadsheet with everyone's social security numbers, date of births, etc. to use for payroll purposes. The President then saves the file on a network folder that others have access to. Even if the President trusts all of the employees, when one of employee's workstations gets hacked, the hacker will now have access to that information too. Therefore, it's critical to control user accounts and what they have access to with network management services.
In all cases, user accounts should only be used by the assigned employee, and those accounts should have permission to access only files and folders they need, nothing more. The control over what an account can do is called the principle of least privilege approach to network security threats, and is one of the most beneficial practices an organization can follow.
The principle of least privilege is the idea that at an employee should have access to only the bare minimum necessary in order to perform their job functions.
How can an organization implement the principle of least privilege?
1. Conduct a "privilege audit": Identify all active user accounts and what those accounts have access to.
2. Adjust user access based on the audit. No one should be using an account with administrator access as their primary account. Additionally, the audit may reveal accounts for terminated employees; these accounts should be disabled/deleted.
3. Start all new accounts with the least amount of access. Add higher-level access when needed to perform a job function. For example, it is usually not necessary for all employees to need remote access (such as a VPN) to the network, but only specific persons.
4. Track/record attempted access to privileged information. Doing so may reveal signs of an attack by the employee or hacker.
5. Periodically perform the privilege audit to verify employees are not accessing information that is confidential or not necessary for their job function.
Hackers accessed 70 million Target customer accounts through an account for an HVAC contractor that had high-level network permissions. By failing to follow the principle of least privilege, Target opened themselves up to this nightmare.
Role-Based Access Control (RBAC)
Depending on the size of an organization, it can be quite time consuming to implement or review the access each employee has to network files and folders. In such cases, organizing employees in groups based on their level of required access will reduce the complexity of controlling access and other network management services you may employ. For example, in Figure 2, a small business may group together the owner and all staff. The administrator group (account) would have access to all system and business files and resources, the owner's group would have access to all business files and resources, while the staff group would only have access to some business files and resources.
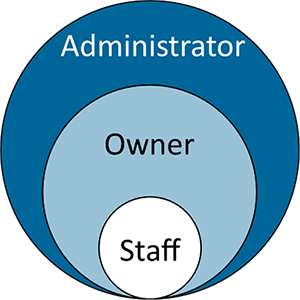 Figure 2: Implementation of RBAC in a small
business. The staff has the most limited access to network resources.
Figure 2: Implementation of RBAC in a small
business. The staff has the most limited access to network resources.For more expansive organizations, additional groups may be created with some or no overlapping access to shared network folders and files
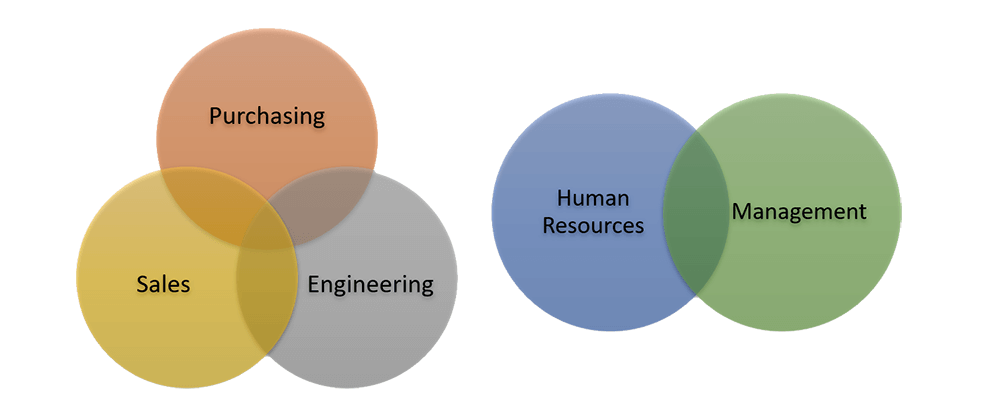 Figure 3: Implementation of RBAC in a
larger organization - Business Departments are segregated
Figure 3: Implementation of RBAC in a
larger organization - Business Departments are segregatedSpeak with a specialist at ICS to discuss a Role-Based Access Control plan or other network management services that are appropriate for your company or organization's size.
Two-factor Authentication
Two-factor authentication is becoming increasingly popular among our network management services, and with good reason.
Almost all systems in place today require some form of authentication, that is, a method of identifying the individual trying to access data. The most recognizable form of authentication is the requirement of a username and password before granted access to a system or network. Though, this requirement is becoming less secure in modern systems. Password theft, either through social engineering techniques or brute force, makes the requirement of passwords a sometimes easy barrier to overcome by hackers or malicious co-workers.
A brute force attack is a trial-and-error method used to obtain information. Such an attack can allow a hacker to submit thousands of guesses a second until a correct password is found.
To secure modern systems against password theft, engineers have developed a method called 'two-factor authentication' or '2FA'. The requirements for gaining access to a system with 2FA are expanded to become:
1. Something you know
2. Something you have
With two-factor authentication included in your network management services, in addition to a password, your identity is verified using a second factor (like your phone or other mobile device), and prevents anyone but you from logging in, even if they know your password. Large customer-facing businesses, such as banks, have popularized a form of 2FA: sending a text message with a code to the account holder's phone and then having them type that code into the website to confirm their identity.
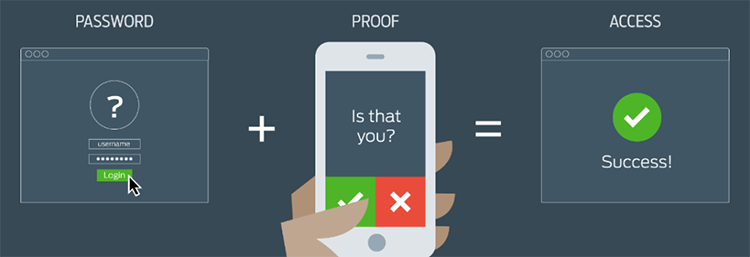 Figure 4: Business productivity is not hindered
with an ICS recommended implementation of 2FA
Figure 4: Business productivity is not hindered
with an ICS recommended implementation of 2FACourtesy of 
If you would like more information on implementing 2FA in your environment, a network security specialist at ICS is ready to discuss this low-cost and high-value solution for your network management services.
Endpoint (Host) Protection
Protecting the endpoint (workstation/server) from being exploited is commonly done with automated protection measures, such as software that quietly waits in the background and warns the user if any malicious files are downloaded or found on the machine. While in the past all that was needed was "anti-virus" software, modern endpoint protection suites encompass many more necessary features and provide a defense for all data coming in or going out of the endpoint, as well as data being processed by the endpoint itself.
As part of our network management services, an endpoint protection solution that ICS installs and recommends for its clients includes the following protection features:
1. Device Protection: Protection against threats and detection of unknown security risks on the computer through heuristics. Also, protection against risks that can compromise personal information and privacy, such as adware, misleading applications, hacking tools, etc.
2. Web Browser Protection: Prevents 0-day exploits in web browsers and blocks 'drive-by' downloads
3. Smart Firewall/Intrusion Prevention: Protects the PC from common security issues by monitoring all communications between it and other computers on the Internet; blocks hackers and other unauthorized traffic, while allowing authorized traffic to pass.
4. Exploit Protection: Recognizes a range of malicious behaviors that are common trademarks of 0-day attacks and subsequently blocks software that exhibits specific behaviors. This feature provides protection against attacks the moment vulnerable software is installed - not if and when a vulnerability is eventually discovered or attacked.
Contact an ICS specialist to discuss our network management services and the extra measures your organization can take to prevent modern-day security issues.


