IT Consulting | IT Support | Managed Services | New Jersey Computer Support Services
Business Continuity Strategy
 Despite the advanced forethought put into reducing data
risk, at some point it can be expected that something catastrophic may happen where employees no
longer have access to the data on the network. What your organization decides to do in such a
case is called a Business Continuity Strategy. Part of this planning involves a way for
your organization to operate using backup equipment, and thus allow for the business to continue
operating.
Despite the advanced forethought put into reducing data
risk, at some point it can be expected that something catastrophic may happen where employees no
longer have access to the data on the network. What your organization decides to do in such a
case is called a Business Continuity Strategy. Part of this planning involves a way for
your organization to operate using backup equipment, and thus allow for the business to continue
operating.
When a disaster disables, wipes out, floods, or in some other way prevents the primary infrastructure from operating, an organization should implement a plan of action to keep the business going. For very small organizations, this may mean something as simple as a file backup service and utilizing an uninterruptible power supply for minimal power backup. In the event of a server crash, the file backup service will already have copied files from the server, which will keep those files safe while awaiting the restoration process onto a new server. While this may take several days to complete, all files will be recovered and thus is a viable business continuity strategy.
Medium-sized businesses usually cannot afford to wait several days for a server or other infrastructure equipment to be replaced, and thus must expand their business continuity strategy to include multiple equipment redundancies. They might choose to include a generator in place for power redundancy, employ the use of two separate internet connection lines from different internet service providers, and have a backup file server located in a geographically different location than the primary file server. While the cost to implement and maintain these redundancies are significant, it allows the whole workforce to continue business operations, rather than being unproductive because of infrastructure failure.
Speak with a member of the ICS Disaster Recovery Team to inquire about the business continuity strategy options available for your organization that will fit your requirements and budget.
Data Breaches
According to the latest Breach Level Index report, there were 918 reported data breaches and almost 1.9 billion compromised data records worldwide in the first half of 2017. Among those records stolen, identity theft accounted for 74% of all data breaches.
Data breaches happen unexpectedly and unknowingly. Staff may inadvertently store or save private information in their email or workstation subfolders. Bank data, credit cards, dates of birth, licenses, and social security numbers are commonly found unencrypted in SMB environments.
"I am convinced that there are only two types of companies: those that have been hacked, and those that will be." (Robert S. Mueller III, 2012)
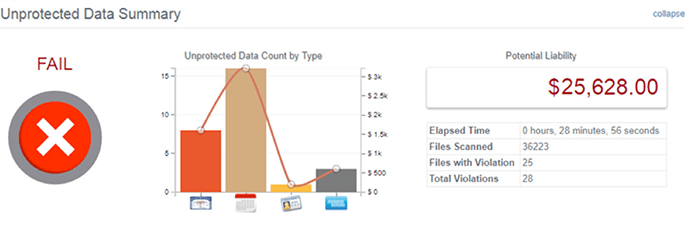 Figure 1: Results of a file server in a 10 employee
business environment
Figure 1: Results of a file server in a 10 employee
business environmentData breaches can cost a lot in both money and customer confidence, and so should be considered when putting together a business continuity strategy. There's the potential cost of replacing credit cards, fines, and compensation for what clients have lost, not to mention investigation costs and audits. Limiting the information on the network accessible to employees, and hackers that gain access to employee accounts, greatly reduces the chances of a devastating data breach. Multiple methods of accomplishing such are discussed in this whitepaper. However, the worst practice is waiting for a data breach to occur, only to realize your business's most valuable data is now being used by malicious entities.
Being proactive and putting data security first will save a lot of time, money, and headache. To identify the specific location of compromising information, ICS will utilize its advanced knowledge of systems and tools to generate a Data Breach Risk Report. This report is presented in an easy to understand format, and will ascertain to what level a machine is at risk.
To request more information on the reports, on business continuity strategy, or what else can be done to protect the network from external threats (hackers) or insider threats (disgruntled employees), contact ICS right away.
Robert S. Mueller III, F. D. (2012, March 1). Combating Threats in the Cyber World: Outsmarting Terrorists, Hackers, and Spies. Retrieved from FBI: https://archives.fbi.gov/archives/news/speeches/combating-threats-in-the-cyber-world-outsmarting-terrorists-hackers-and-spies


